CryptoLocker Evolves into a Worm to Spread Independently
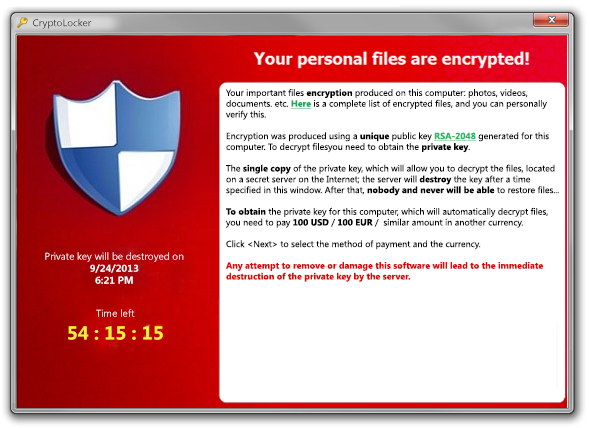
The pernicious ransomware CryptoLocker, which encrypts all files on your hard drive, has evolved from a Trojan horse into a worm, and can now spread via removeable disks like USB sticks, according to new research.
Security company Trend Micro has just published a blog about the discovery of a CryptoLocker variant which it calls "significant" as it means the malware can now be easily spread, unlike previously known CryptoLocker variants.
It means that CryptoLocker will now be able to spread independently, under its own steam, and not rely on the criminals behind it sending out spam emails. According to security expert Graham Cluley, this "might make it easier for CryptoLocker to infect PCs across your organisation."
Copycat
The differences between the origninal and the newly discovered variant have led some researchers to believe this is the work of a copycat, rather than a new version created by the gang behind the original.
First discovered in September of last year, CryptoLocker is a piece of malware known as ransomware, which infects your PC, encrypts all the files on your hard drive and gives you a limited amount of time to pay a ransom before losing your files forever.
Reports last month indicated that 250,000 PCs around the world had been infected – mainly in the US and UK – but the discovery of this new variant could see that figure skyrocket.
Variations
Until now, CryptoLocker has been spread via spam email, with victims tempted to download an attachment or click on a link to a malicious website.
As well as the difference of how a system can get infected, the new version of CryptoLocker shows other variations. According to Trend Micro the new variant now poses as an activation key for popular software such as Adobe Photoshop and Microsoft Office.
Pirated copies of these pieces of software are shared widely on peer-to-peer file-sharing sites and the criminals behind the updates version of CryptoLocker could be looking at this as a new, and highly-lucrative, way of spreading the malware.
However there is some good news according to Trend Micro. The new variant forgoes the original's domain generation algorithm (DGA) system, which made it difficult for your security systems to block the domains CryptoLocker was contacting, and instead the new variant's command-and-control (C&C) servers are hardcoded into the malware.
"Hardcoding the URLs makes it easier to detect and block the related malicious URLs. DGA, on the other hand, may allow cybercriminals to evade detection as it uses a large number of potential domains," said Trend Micro's Abigail Pichel said.
© Copyright IBTimes 2025. All rights reserved.






















