Hackers turn up the heat by revealing Aga ovens can be hijacked via text message
Total Control 'smart' cooker ends up looking silly at the hands of a penetration tester.

Cybersecurity vulnerabilities have been uncovered lurking in applications used by a high-tech Aga cooker that can give hackers the ability to potentially steal user data, mess with temperature levels and even turn the oven on and off.
According to Ken Munro, a security expert at Pen Test Partners, the issues were found on its Range cookers with 'Total Control', which lets users control the cooker's heat levels with the use of a connected mobile application (iOS and Android), text message or through a web portal.
He said disclosing of the flaw was a "train-wreck".
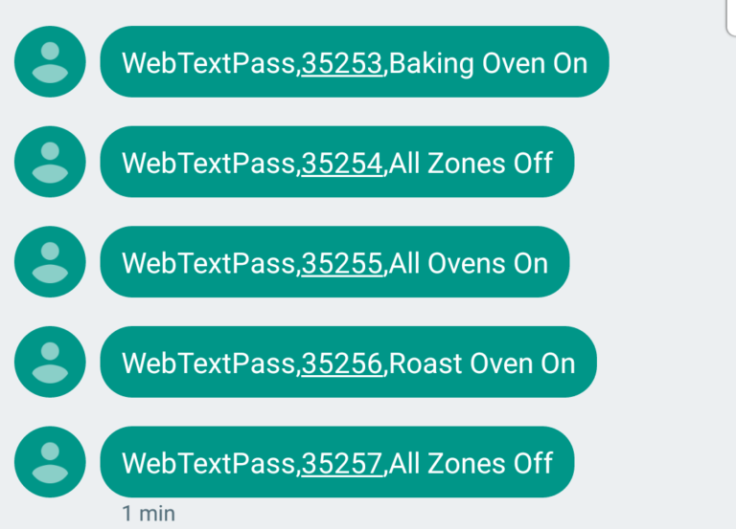
"All you have to do is simply send a text message to the Aga," Munro said. "We didn't, but it would be trivial for less ethical culinary threat actors to do so.
"You probably know it takes hours for an Aga to heat up. Switch it off, annoy the hell out of people."
The researcher, who has a long history of exposing bugs within Internet of Things (IoT) devices, said he decided to analyse Aga's cybersecurity when looking for a replacement for his own product. "We found that even Agas can be hacked. Seriously," he revealed.
Munro found the login and registration pages on the Aga 'Total Control' application – marketed since 2012 – was sending customer data in an unprotected format and had weak password rules because the service has a policy that keeps credentials at five characters long.
Upon further analysis, the researcher found the product in question , the Rangemaster, comes with a physical module as standard that not only has internet access but can receive text messages. The major criticism was texts were not being validated or authenticated correctly, he said.
In his disclosure this week (12 April), Munro stated: "There's no link sent to validate the number or the account. Nothing. Yes, hackers could turn other people's Agas off. One could also power up people's Agas when they're not looking, wasting electricity.
"They draw around 30 Amps in full heat-up mode, so if you could switch enough Agas on at once, one could cause power spikes. That's a bit fanciful though." So, the problems were real, but actually getting the company to acknowledge and fix them proved difficult.
"We tried Twitter, every email address we could find and then rang them up," he said, adding: "No response to any of the messages we left." Pen Test Partners made first contact on 30 March this year however by 9 April Aga had blocked their account on social media.
"Come on Aga, sort it out. This isn't acceptable," Munro complained. "Get rid of the silly SMS-based remote control module and put in a nice secure Wi-Fi enabled module with mobile app."
In a statement to the BBC, a spokesperson said: "Aga Rangemaster operates its Total Control phone app via a third party service provider. Security and account registration also involves our [machine to machine] provider." The statement stressed the firm takes security issues seriously.
© Copyright IBTimes 2025. All rights reserved.






















