Hacking Team hacked: 10 things learned from massive data breach of spying company
Controversial seller of spying software Hacking Team has been the focus of a huge amount of attention of the last three days since a massive leak of sensitive internal data was posted online.
What is Hacking Team?
Italian company Hacking Team sells sophisticated spying software to governments and law enforcement agencies around the world.
They have been criticised for selling their services to repressive regimes with questionable human rights records in countries such as Sudan, Bahrain and Kazakhstan.
On 5 July a trove of 400GB of data stolen from the company was posted online by an unknown hacker. This included sensitive documents, government tender details, client invoices, internal emails, and crucially, source code and explicit details on how the mass surveillance software operates.
In the wake of the data breach, the company has attempted to defend its actions, claiming it has "broken no laws and acted in a completely ethical manner" despite widespread condemnation of its practice of selling its powerful surveillance tools to countries which have less than stellar human rights records.
With over 400GB of data to sift through, there are still many revelations to come, but here we round up 10 snippets of info which may have passed you by to date.
1. Hacking Team has terrible OpSec
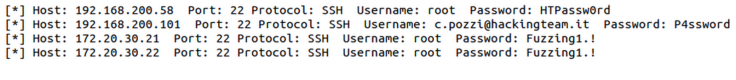
According to the leaked data, the employees at Hacking Team were clearly not overly concerned about becoming the target of an attack themselves, as the passwords they used were extremely weak.
Christian Pozzi, a security engineer at the company who briefly tried to deny the validity of the leak on Twitter before having his account hacked, used the password "Passw0rd" across all systems, according to the leaked documents.
If you are wondering how someone could make off with 400GB of data without anyone noticing, the fact that Hacking Team's servers used passwords like "P4ssword" and "HTPassw0rd" might give you some indication.
2. Antivirus failure
As part of the Hacking Team leak, the anonymous hacker behind the attack leaked the source code for the company's surveillance tools. Running some of Hacking Team's signatures through VirusTotal showed that none of the 56 antivirus solutions it checks flagged the malware.
While we will no doubt begin to see these signatures flagged by security companies in the coming days and weeks, it just highlights how broken antivirus is.
3. iPhone remains secure (for now)
According to security expert Bruce Schneier, Hacking Team has no exploits to hack iPhones that are not jailbroken. However, documents within the leaked trove of data show that the company has the ability to jailbreak and infect an iPhone when it is connected to a malware-infected trusted computer.
Additionally, a leaked email referring to a demonstration for the Kurdistan Region Security agency suggests that support for non-jailbroken iOS devices was being worked on by Hacking Team - though that shouldn't come as much of a surprise.
4. Child porn references in source code
Following the massive data leak, some researchers discovered child porn references within the source code for the company's Remote Control System (also known as Galileo), which led some to suggest that Hacking Team may have built and sold a "child porn fabrication tool".
The code relating to the tool was uploaded briefly to Github before being removed, and experts have since backed away from the initial claim, and have instead suggested that it was simply there for demo purposes rather than anything more nefarious.
Come on people, that "childporn" Hacking Team thing is clearly not for planting evidence. Let's not spread misleading rumours.
— Claudio (@botherder) July 6, 20155. Finding Hacking Team targets
Hacking Team surveillance software has been used by law enforcement agencies and governments around the world to monitor citizens. Many of those citizens are thought to be activists and journalists, but in the wake of the data leak, the users of the Galileo software are likely scrambling to remove traces of its presence from infected devices.
In a bid to prevent this from happening, some developers have launched what they call the Hacking Team Sweeper which aims to identify signatures associated with the company's software and write scripts to automate the discovery of it. It is seeking help from the research and security community to identify these signatures.
6. DEA: We want all the Columbian traffic
One leaked email shows that the Drugs Enforcement Agency (DEA) was looking to integrate Hacking Team's Remote Control System with another spy tool which allowed them receive "all the traffic for Columbian ISPs".
It is unclear what this other spying tool is, but the leaked email was sent on 9 June, 2015 following a meeting between a Hacking Team representative and the DEA's man on the ground in Bogota.
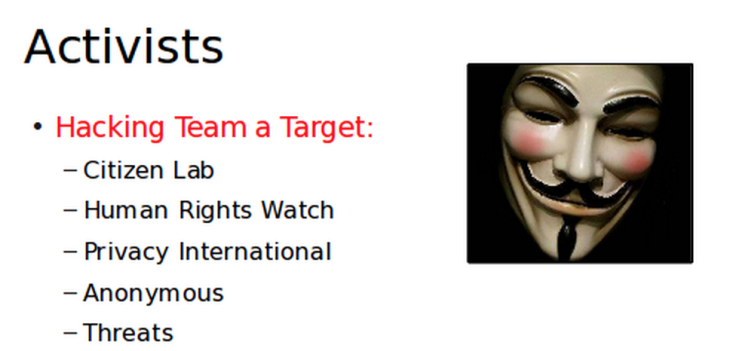
7. Hacking Team's enemies
A leaked document lists groups which Hacking Team saw as a threat to its business. As well as groups like Human Rights Watch, Privacy International, and Citizen Lab which have been very vocal in their condemnation of the company's willingness to sell to oppressive regimes, the hacktivist group Anonymous is also listed among Hacking Team's threats.
8. CEO David Vincenzitti jokes about a leak
In an email sent less than a month before the massive data dump, Hacking Team CEO Vincenzitti joked with company employees about what would happen if someone leaked information:
"Imagine this: a leak on WikiLeaks showing YOU explaining the evilest technology on earth! :-). You would be demonised by our dearest friends the activists, and normal people would point their fingers at you."
Oh dear.
9. Brazil could be Hacking Team's biggest customer in 2015
According to a projection for revenues in 2015, the Brazilian federal police force is/was set to be the company's biggest customer with a potential windfall of €1.7m (£1.22m). Next comes Kazakhstan with potential revenue of €1.5m and Ethiopia contributing up to €1m to Hacking Team's coffers this year.
Rounding out the top five revenue generators for the company in 2015 are Columbia and Denmark, both of whom are using US-Israeli company Nice Systems.
10. Mexico however is by far its biggest client to date
#HackingTeam revenues per country. Over €3 million and you get coloured in green. pic.twitter.com/uKbqTflUqw
— Richard Tynan (@richietynan) July 6, 2015While Brazil may represent the future for Hacking Team, Mexico has been its biggest customer to date, paying out $6.3m (£4.1m) to the company. Up to 14 separate Mexican states have signed up with Hacking Team to date, and the Mexican interior ministry is the most recent recruit.
At $1.9m spent, Italy is the next biggest state customer, where Hacking Team is headquartered. This is followed by Morocco, Saudi Arabia, Chile, and Hungary.
© Copyright IBTimes 2025. All rights reserved.






















