'Red October' Infrastructure Dismantled Hours After Being Made Public
The people behind one of the most sophisticated cyber-espionage attacks ever carried out began dismantling its infrastructure hours after it was made public.
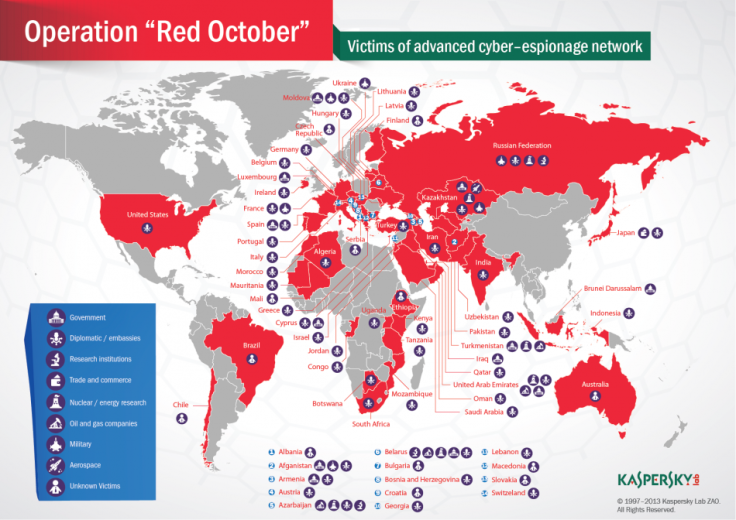
On Monday, 14 January, Kaspersky Labs published details of malware called Red October or Rocra, detailing how it attacked governments, diplomats and scientific organisations with highly-targeted attacks which were able to steal huge amounts of sensitive and classified data.
Red October had been in operation for more than five years without being discovered, but within hours of the malware being made public, the people behind the cyber-attack began dismantling it:
"The attackers started dismantling the infrastructure last night [14 January] at 11pm GMT, by taking down some of the C2s [command servers] and superproxies," Costin Raiu, senior security researcher at Kaspersky Labs, told TechWeekEurope.
"At the same time, ISPs have shut down some of the C2s while registrars have killed the domain names. Currently, there are still some active servers, however, the infrastructure is severely disrupted and mostly not working anymore."
The complexity of Red October has been compared to that of Flame, which was discovered last year targeting networks in the Middle East. The scale of the Red October malware was enormous, with more than 60 domain names and several server hosting locations in different countries (mainly Germany and Russia).
The Command & Control server infrastructure was actually a chain of servers working as proxies in order to hide the location of the main "mothership" server.
Publish
Kaspersky Labs are due to publish more data on the malware this week which could shed some light on where the attack originated and the scale of the information stolen.
Another security firm has weighed in on the matter, with F-Secure pointing out that the methods used were very much like any other targeted corporate espionage attack.
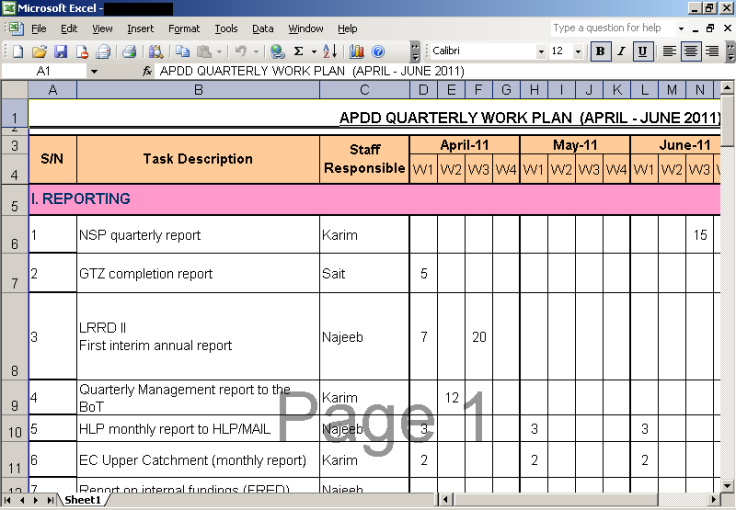
"The attackers use exploit documents with credible looking content so the victim will open the file, drop a malicious payload to the infected device, and start mining all information they can from the infected system," the company said in a blog post entitled Every Month is Red October.
The company adds that the exploits used were "not advanced in any way," with the attackers using well-known Word, Excel and Java vulnerabilities.
F-Secure also posted some of the documents (above) used in the attacks, saying that while the large scale and time span of the Red October attack is "interesting", the truth is "companies and governments are constantly under similar attacks from many different sources. In that sense, this really is just everyday life on the internet."
© Copyright IBTimes 2025. All rights reserved.