Dangers of spear phishing: US woman sextorted by hacker who hijacked her social media accounts
Hacker hijacked woman's Facebook, LinkedIn and iCloud accounts to blackmail her into engaging in sex acts.

Forget stealing financial details or trade secrets – cybercriminals are now using spear phishing techniques as a means of blackmailing internet users into performing sexual acts on camera.
A woman in the US, who goes by the username Zedevile, revealed on Reddit that she lost access to all of her online accounts and was locked out of her main email account after falling victim to a serious cybersecurity scam that specialises in targeting small groups of people or individuals. The hacker threatened to expose her details and post compromising photos of her on social media if she didn't strip and perform sexual acts on camera.
Zedevile's nightmare, verified by IBTimes UK and how-to website Comparitech, began when a hacker posing as a female acquaintance contacted her on Facebook asking her to vote for a modelling competition online. In order to do this, the friend asked Zed to hand over her Apple ID and Google Account ID so that she could be added to a Facebook group to vote for the group.
She agreed, but once in the group, her friend told her that there was a bug affecting Facebook that wouldn't let her add anyone else to the group. She needed to remove Zedevile from the group to fix the error, and to do that, she would need Zedevile's password.
Don't trust anyone who asks for your passwords
"It's ruined everything, and could I please please give her my password for one quick second please just so she can take me off the system and at least go back to the way it was? Her career was at stake for goodness sake, she begged. After going back and forth for a bit.. I fucked up. I trusted her. I thought there was no harm and I would just change the password right after. It was the password to a Gmail ID I never use anyway, except for signing up on random websites where I don't want to get their spam mail but need to create an account, you know how we all have one of those," Zedevile wrote on the Black Mirror subreddit.
Zedevile complied and then went to a work meeting. Just 25 minutes later she came out of the meeting, went back to her desk and discovered that she had been logged out of her main Hotmail email account by someone signing in from Pakistan, because the unused Gmail account had been the recovery email for her Hotmail.
Because he hijacked her Hotmail account, the hacker now had full access to her Facebook, LinkedIn, Amazon, Apple ID and online bank accounts, and within minutes he began changing all of her details to lock her out of those accounts, including her recovery phone number, email, birthday, and security questions for her Apple ID.
Zedevile used her boyfriend's Facebook account to contact the hacker, who told her that he didn't want money and didn't care if she tried to report him to the police. The hacker had seen private photos of her stored in her iCloud account (remember the Fappening iCloud hacking scandal?) and concluded that she was a "slut".
Hacker demanded she perform sexual acts on camera
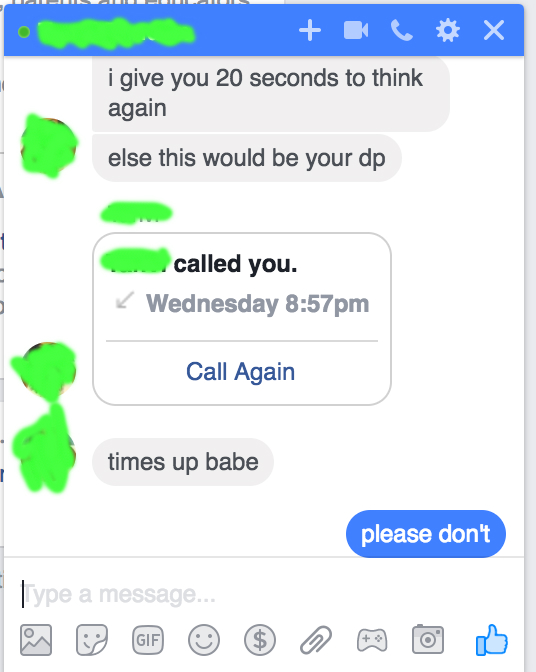
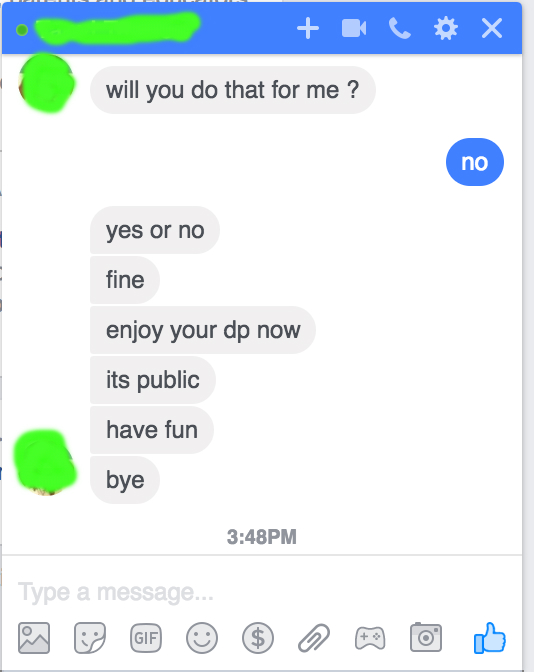
"I asked him if he wanted money, anything of the sort. He said he could buy me with money, so I should drop that. So I asked him what he wanted from me. He asked me to take my clothes off and touch myself in front of him on FaceTime. Satisfy him. Only then would he give my accounts back," she said.
When Zedevile refused, the hacker took a compromising image from her iCloud account and made it her profile picture on Facebook so that everyone could see it. Her boyfriend and friends began monitoring her account and reporting each image as it appeared, and they managed to get her profile deactivated by Facebook within 10 minutes, but not before at least 15 contacts saw the compromising images.
She spent the next month trying to get her accounts back. Facebook, Instagram, Apple and Google customer service were all helpful and she was able to recover those accounts, but she said that Microsoft and Snapchat both had "terrible customer service", and after days of trying, she had to give up ever getting her Hotmail email account back.
Zedeville also discovered when she got her Facebook account back that the hacker had messaged 25 women on her account posing as her and managed to trick one friend, who also lost all of her accounts too.
"Do not ever give your personal information away, even to a close friend or loved one. Gotta be sure you trust them. Anything can happen. I don't even trust the cloud anymore. F**k this guy for ruining my faith in humanity. I hope they catch the mother f***er," she said.
Don't ignore the dangers of spear phishing
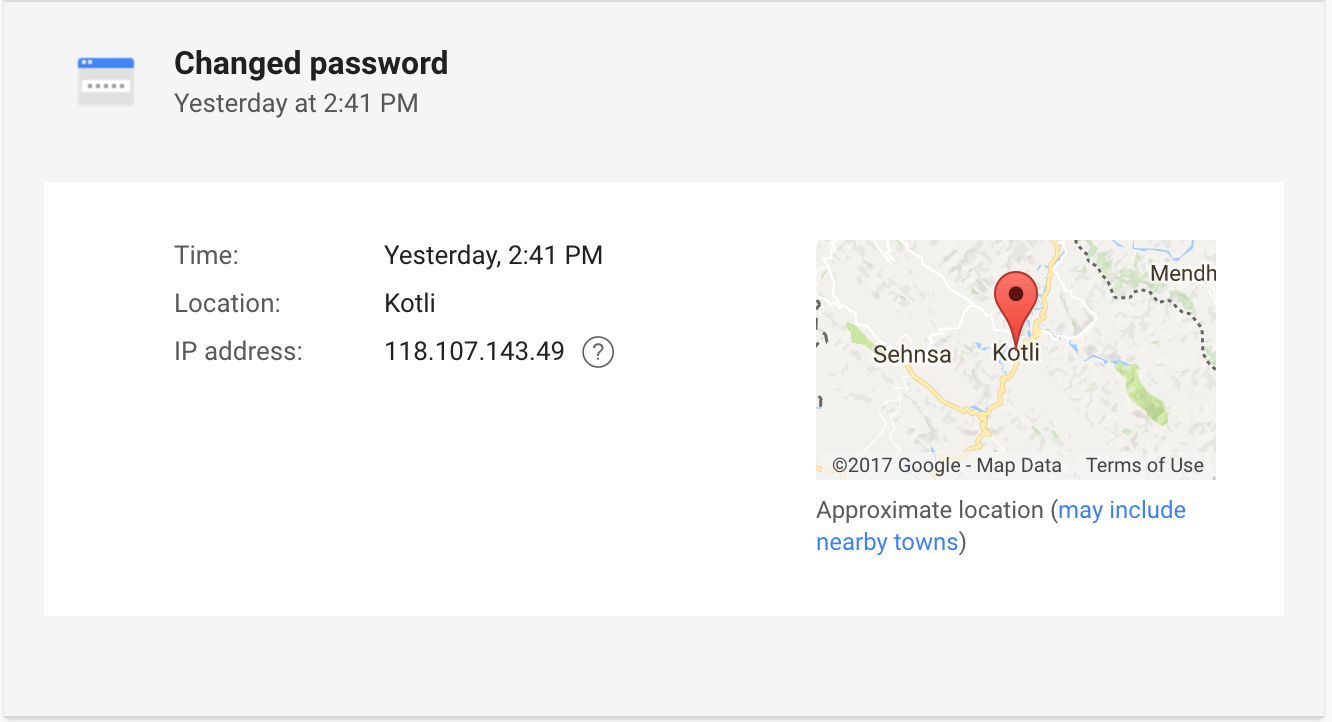
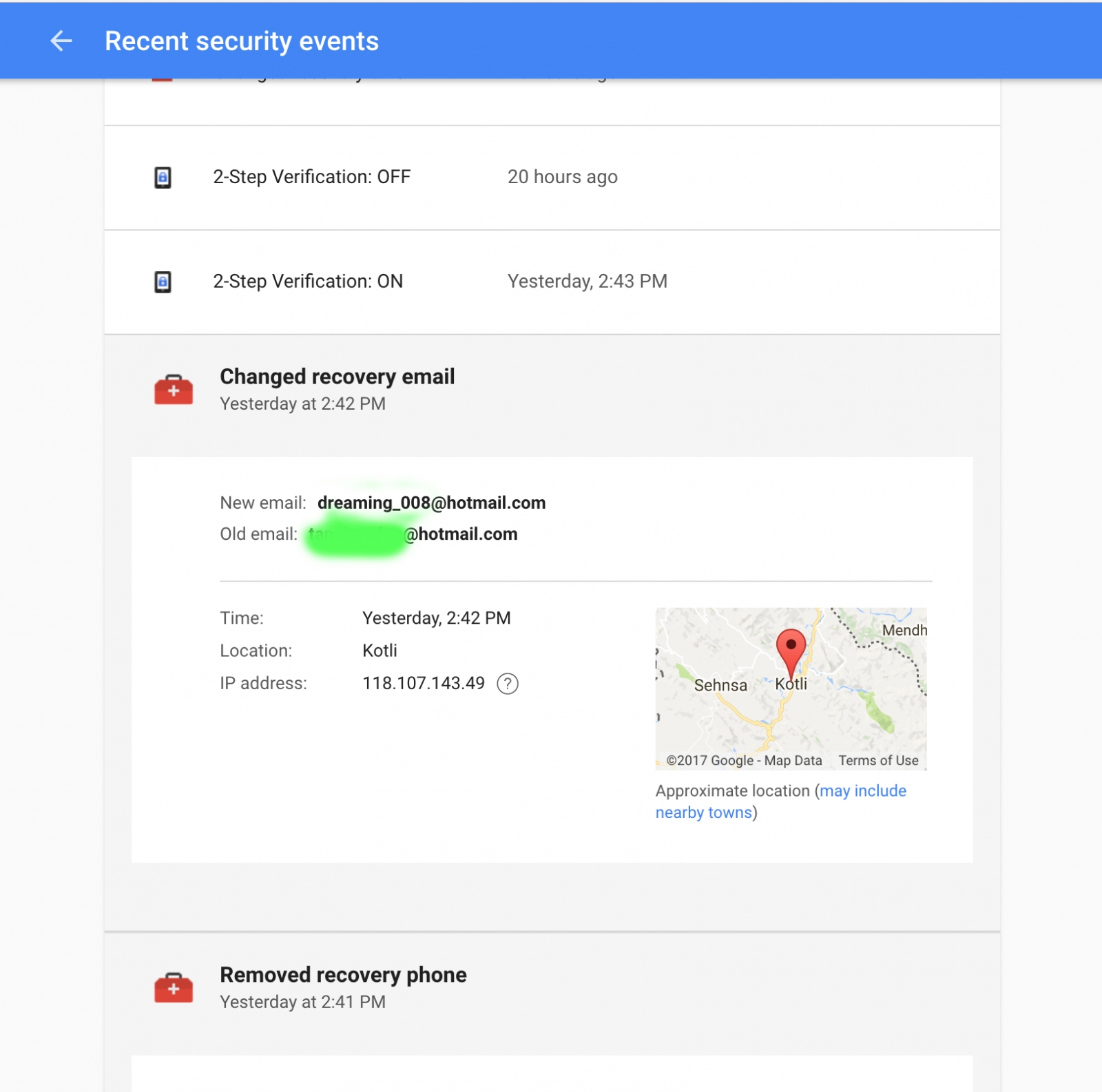
Spear phishing is far more dangerous than regular phishing attempts, which usually include malicious links in fake emails. Cybercriminals who engage in spear phishing do their best to impersonate an actual person that the victim knows in order to trick them into releasing sensitive information.
Spear phishing is now becoming a popular cybercrime because the returns are far more lucrative than trying to trick the general masses. For instance, in September 2016 electrical cable manufacturer Leoni AG lost €40m ($42.4m, £33.7m) overnight after their CFO was tricked into transferring funds into a hacker's bank account.
And in April 2015, toy maker Mattel had to seek help from the Chinese government to halt a transfer of $3m after hackers with intimate knowledge of Mattel's stringent funds transfer policy tricked an executive into wiring the money to the Bank of Wenzhou in Zhejiang province.
Comparitech advises that users guard their passwords jealously and build strong passwords containing a random combination of letters, numbers, and symbols that's at least 12 characters long. Users are also strongly advised to always enable two-factor authentication or two-step verification on all accounts where the service is offered, and not to rely on email verification.
And of course, beware of regular phishing scams as well. Don't click on links or open file attachments from any emails or web pages you don't recognise. "On desktop browsers, you can hover over a hyperlink to display where it actually leads in the bottom-left corner of the browser window. Be wary of subdomains used to make URLs look legitimate. For example, PayPal's website is 'www.paypal.com'. An imposter website can put 'paypal' as its subdomain and an official-looking top level domain so it uses the URL 'paypal.official-paypal.com'," advises Comparitech researcher Paul Bischoff.
© Copyright IBTimes 2025. All rights reserved.






















