Flame Virus Malware 'Developed By a Government or Nation State'
Update: Not related to FLAME Lua software
The Flame malware was "developed by a government or nation state with significant budget and effort, and may be related to cyber warfare activities," claims a report from the Hungarian Laboratory of Cryptography and System Security (CrySyS).
"The complexity of The Flame, geography & targets leave no doubt this malware was state-sponsored," Eugene Kaspersky, chairman and CEO at Kaspersky Lab, added on Twitter.
The Flame Virus has been described as the most complex malware ever found online. It has gone undetected for over two years and has been stealing sensitive information during that time.
"We do have timelines as early as 2010. However, we found a file online that is unique to Flame and that goes back to 2007. That matches how long we think Stuxnet and Duqu had been in development. We do believe they were parallel projects," Roel Schouwenberg, a researcher at Kaspersky, told IB Times UK.
CrySyS Labs, which is part of the Budapest University of Technology and Economics, began to analyse the Flame malware early in May and produced a detailed 63-page report.
Graham Cluley, senior technology consultant at security firm Sophos, was more cautious in his analysis but admitted the Flame Virus would have taken a lot of effort to produce.
"I don't think you can say it has to have been state sponsored because it's very hard to prove things like that. It was the same with Stuxnet. However, in all likelihood it is a project organised by someone with those kinds of resources because the code is so large and would have taken a lot of development," he told IBTimes UK.
"That's a lot of work wasted because it's now been detected and everyone knows it is out there."
If the intrusions are state sanctioned, the question remains as to which country is behind them.
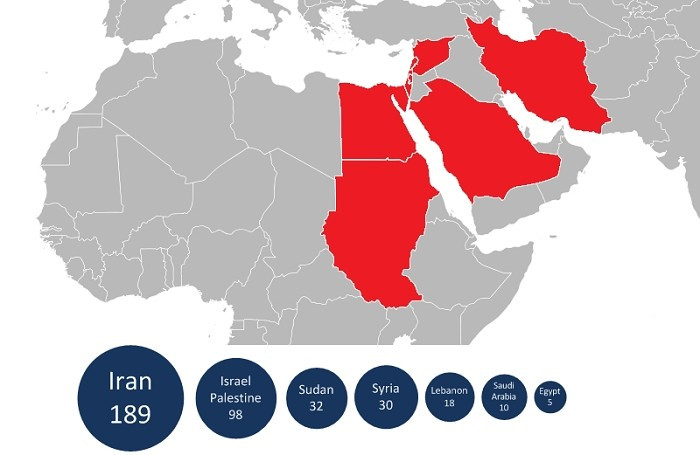
The attacks appear to be centred on the Middle East based on a report from Kasperky Lab, although some European breaches have been noted.None of the experts in the security field have been quick to point fingers at likely targets.
"There is currently no strict evidence pointing to a specific country or even a region that might be related to the development or the development of this cyber attack," said Vitaly Kamluk, chief malware expert at Russia's Kaspersky Labs.
"It isn't very clear what all these targets have in common. Stuxnet had a goal and Duqu had a group of less than 50 targets all in Iran's nuclear program. We believe the Flame virus was commissioned by same nation state as those two pieces of malware but we haven't been able to find the common ground yet," said Schouwenberg.
Cluley also warned of only looking at those cases in the Middle East.
"I would be cautious about saying it's definitely targeting the Middle East. Kaspersky only has about 200 cases documented in Iran and down in seventh place in the same list of results is a Middle East country with five cases detected. Crysys also found cases of Flame in Hungary so attacks have happened outside that area," he said.
"Our participation in the investigation efforts was justified by the possibility that one or more European countries may be affected by the threat. Later, we received information that, indeed, sKyWIper [aka Flame] is active in some European countries, including Hungary, our home country," the report from CrySyS Labs said.
Coincidentally, a piece of networking software called Flame already exists and it is based on the same Lua scripting language as the malware. It is not known if the malware's authors stole code from the Flame network measuring tool but that would throw doubt on the idea that the attacks were state sponsored.
Cluley said it wouldn't be the first time that someone had taken a piece of software and modified it for their ends.
"A lot of programmers borrow. If someone's done a lot of work you'll be tempted to use that library," he said.
UPDATE 30 May, 2012: Kaspersky Lab has ruled out a link between the networking software called Flame and the Flame Malware Virus.
"Interestingly, the name picked by us fully matches that software, which also uses LUA for implementing business logics. The FLAME software is used to measure network characteristics by deploying measurement agents and collecting data in a central database. Despite some similarities, we think that this software is unrelated as it serves different objectives. Besides the LUA engine, the core of communication in FLAME is XMPP protocol, which is not used in the Flame malware," said Alexander Gostev of Kaspersky Lab.
"The authors might have been inspired by the FLAME project and re-implemented similar architecture - only for the different goal, or this is all just a coincidence. We don't have any other reason to think that it is somehow related to the Flame malware."
Must Read:
Stuxnet, Malware and Wikileaks: How Cyber Warfare is a Very Real Threat
© Copyright IBTimes 2025. All rights reserved.





















