Shawshank 2.0: Crafty inmates built computers, went online and committed identity fraud
Inmates at a prison in Ohio managed to build their PCs and access the internet without being caught.

Forget Orange Is The New Black – prisoners at a jail in Ohio, Florida, have gone above and beyond in creativity by building their own computers and hiding them in the prison's ceilings in order to access the internet. The inmates used the computers to commit identity fraud so they could order credit cards, with the intent of using the funds to help start an illegal business.
Prison authorities were baffled when the Florida prison department's computer network support team received an alert that a computer was not only exceeding the daily internet usage threshold set for prison network computers, but was also trying to bypass proxy servers to access restricted content.
When they checked the login being used, they found that the user account belonged to an Ohio Department of Rehabilitation and Correction employee, but his account was being used even on his days off.
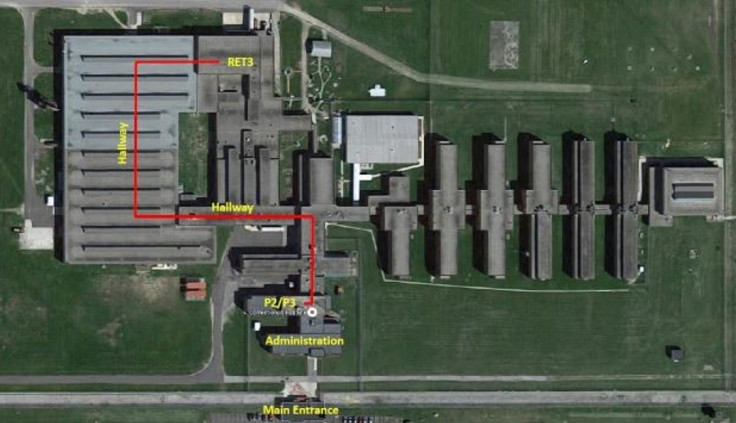
Further investigation showed that the internet connection was coming from somewhere in the Marion Correctional Institution in Marion County, Florida, which is a men's-only minimum and medium security prison.
According to local Ohio newspaper Cleveland.com, the mischief was managed by inmates Adam Johnston and Scott Spriggs, who were part of a programme in which inmates were supposed to be disassembling old unwanted PCs so that useful parts could be recycled, provided by a Cleveland-based non-profit called RET3.
Inmates approved to dismantle PCs and use software

Since the technology was valuable, a prison employee asked the inmates to set aside some of the newest computers for the prison to keep, and the prison's warden Jason Bunting had personally given approval for inmates to use software to wipe the computers and install new operating systems.
Johnston and Spriggs took some of the salvaged spare parts and built two computers, which they then hid in the ceiling of the administrative building and then ran cabling to connect the computers to the main prison network.
The inmates stole a prison employee-turned-contractor's account by watching over his shoulder as he typed in the password. They used the account to look up inmate records, but also to go online and access any website they wanted to look at, such as articles on making homemade drugs, plastic explosives and fake credit cards. The computers contained downloaded software, videos and pornography.
By searching the inmate records, Johnston obtained the social security number and other personal details about an inmate, and then applied for five debit and credit cards in the individual's name by using the address of his mother's neighbour. He used the computer to send messages to his mother and other individuals to set this up.
Prison tried to cover the issue up
But what makes the case even more unusual is the fact that the staff of the Marion Correctional Institution apparently discovered the incident in July 2015, but then decided not to report it to the state authorities.
By the time state troopers descended on Marion Correctional Institution, the prison's staff had removed the computers and all other materials from the crime scene. One employee has since resigned from the prison.
"It surprised me that the inmates had the ability to not only connect these computers to the state's network but had the ability to build these computers," Ohio Inspector General Randall J. Meyer told local TV channel WRGB CBS6 Albany.
"They were able to travel through the institution more than 1,100 feet without being checked by security through several check points, and not a single correction's staff member stopped them from transporting these computers into the administrative portion of the building. It's almost if it's an episode of Hogan's Heroes."
© Copyright IBTimes 2025. All rights reserved.






















