Cerber: Terrifying Russian ransomware speaks bitcoin demand to blackmail victims out loud

Security researchers have exposed a new form of ransomware called 'Cerber' that not only encrypts sensitive files on your computer but also comes with a text-to-speech function that will literally read you the demands of the cybercriminal out loud. Thought to have surfaced from Russian underground malware forums, the malicious Windows-based programme is so effective that experts claim there is no known way of decrypting the files without paying the fee.
While much remains unknown about this new-found threat, analysis shows that Cerber has the characteristics of 'ransomware-as-a-service' (RaaS) which is a lucrative business model for malware creators selling full off-the-shelf packages. Traditionally, the original coder will take a percentage of the ransom fee once the victim pays up.
"When infected, a victim's data files will be encrypted using AES encryption and will be told they need to pay a ransom of 1.24 bitcoins or $500 to get their files back. Unfortunately, at this point there is no known way to decrypt a victim's encrypted files for free," explained Lawrence Abrams, a malware expert at BleepingComputer who has analysed the Cerber source code.
When it first takes hold, the ransomware will check what country the victim's computer is from. Interestingly, the research shows that it is set to terminate if the user is living in one of 12 former soviet countries including Georgia, Russia and Uzbekistan. Next, Cerber will show the user a fake system alert and once they restart the system it will begin the mass encryption process. According to the analysis, Cerber then creates three ransom notes that each contain detailed instructions on what has happened and links to a Tor-based decryption service where users can pay a fee to regain access to their files. Alongside the notes is a warning: "That which does not kill me makes me stronger."
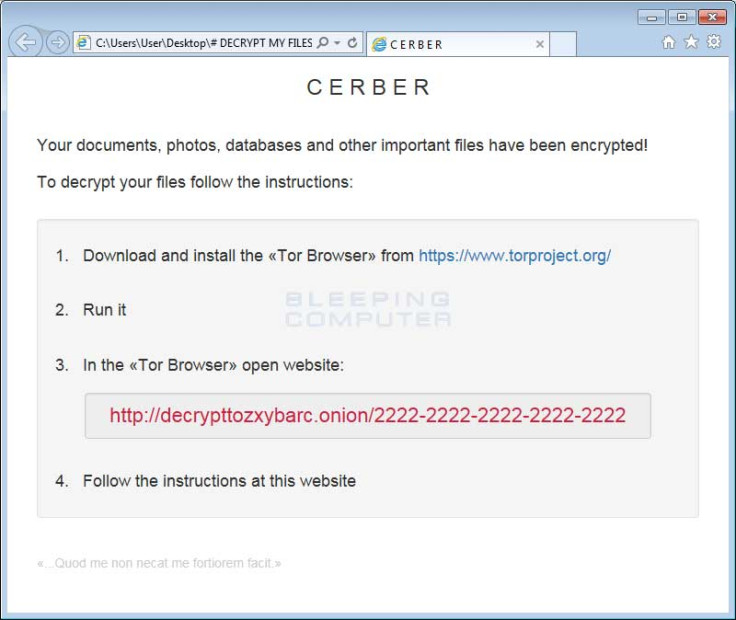
A vocal warning
However, what differentiates this ransomware from the other sophisticated programmes in existence is the fact it will cause the victim's computer to speak to them. Yes, it will literally read you a message, repeatedly saying that your files are now encrypted.
"One of the ransom notes that Cerber creates is a bit more 'special' then the others. The #DECRYPTMYFILES.vbs file contains VBScript, which will cause the victim's computer to speak to them," explained Abrams.
The ransom note contains a link to a Tor-based 'onion' website called 'Cerber Decryptor' and provides a step-by-step guide on how to pay the ransom with the cryptocurrency Bitcoin. Additionally, it warns that the ransom fee will double if not paid within a week.
Unfortunately for anyone infected with Cerber, the current research states that there's known way to decrypt the computer files for free. "If you are a victim of this ransomware then your best option is to restore your files from a backup," Abrams added.
While it is now under analysis by multiple security firms, the ransomware was first uncovered by two independent researchers under the Twitter handles @BiebsMalwareGuy and @MeegulWorth.
As the debate rages on about should victims of ransomware pay the money, successful cyberattacks using this form of tool continue to spike. Most recently, a major US hospital paid an unknown hacker $17,000 after a ransom-style attack locked down a spate of crucial computer systems. In light of this, Cerber is definitely one to watch, yet hopefully never have to listen to, in the coming months.
© Copyright IBTimes 2025. All rights reserved.






















