Suspected Saudi Aramco Malware Created by Amateurs
The creators of Shamoon malware suspected of being behind the Saudi Aramco attack were amateurs according to security experts.

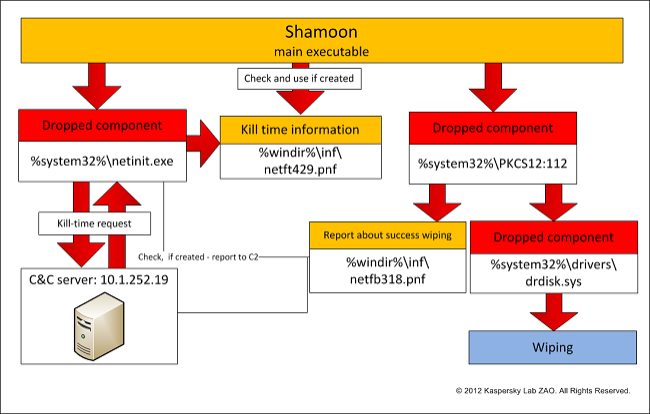
"Silly errors" like using an upper case S rather than a lower-case s in the code, and "crude" solutions to programming issues indicated to security experts at Kaspersky Lab looking into the Shamoon virus, that it had been created by amateurs.
On 17 August it emerged that Saudi Aramco, the world's largest producer of crude oil had been hit by a cyber-attack which knocked 30,000 computers offline and forced the entire system to shut itself off from the outside world.
It is suspected by many that the Shamoon computer virus was used in the attack, and in a subsequent attack on another energy company in the Middle East, RasGas, two weeks later. While the security experts at Kaspersky Lab cannot confirm if Shamoon was responsible, its investigation into the virus has found that it was developed by amateurs:
"We've got other clues that people behind creating the Shamoon malware are not high-profile programmers and the nature of their mistakes suggests that they are amateurs, albeit skillful amateurs, as they did create a quite practicable piece of self-replicating destructive malware," Dmitry Tarakanov, researcher at Kaspersky Lab said on the Securelist blog.
During his investigation in Shamoon, Tarakanov discovered a fragment of a picture embedded in the code, which was of a burning US flag (see above). This clue was not hidden and was there to be discovered, according to Tarakanov:
"The fact that they used a picture of a fragment of a burning US flag possibly shows that the motive of Shamoon's authors is to create and use malware in a politically driven way. Moreover, they wished that their protest which was embedded into the malware would not go unnoticed."
Drivers
The creators of this malware used legitimate drivers created by legitimate developers during its creation, and rumours that this was happening within the malware community have now proven to be true. "Developers of drivers should always keep in mind that cybercriminals and other people who create malware search for covert ways to access a system's [kernel]."
The question of who was behind the Aramco attack remains unsolved at the moment, despite one group claiming responsibility.
Following the attack, a group calling themselves Cutting Sword of Justice claimed responsibility, saying it was a warning to the Saudi government and in particular the House of Saud, the ruling royal family of Saudi Arabia.
Last week it was reported by Reuters that one or more insiders with high-level access are suspected of assisting the hackers, according to sources familiar with the company's investigation.
The attackers used a piece of malware - possibly Shamoon - which spread through the company's network, wiping the hard drives of 30,000 computers, in what is one of the most destructive cyber-attacks against a single company in history.
Debacle
However, there is no proof this claim is valid, and security researcher with Finnish company F-Secure, Seán Sullivan is sceptical about the validity of the group's claim:
"Just like last week's claim that the Apple UDID debacle lies at the FBI's door, the latest conspiracy theory that the previously unknown 'Cutting Sword of Justice' are behind attacks on Saudi Aramco is completely unsubstantiated."
The group has threatened to release sensitive documents it says it stole during the attack, but no such documents have been released so far.
"There is no evidence linking the group to this highly devastating attack, which is as likely to be an inside job as it is the work of industrial competitors looking to influence oil prices.," Sullivan added.
With RasGas being attacked shortly afterwards in similar fashion, energy companies in the Middle East will be nervously looking over their digital shoulders for the next attack.
"There is an argument that this is indeed a continuing threat to oil companies in the Middle East. Simply put, attacks like this will influence pricing [of oil] and as such, cyber-attack is a method of influence open to those wishing to shake the market," Sullivan says.
However, the real worry here, according to the F-Secure security expert, is that it doesn't matter who is behind the attack but that 30,000 computers have been damaged: "Whatever the motive this is a security failure of enormous proportions."
© Copyright IBTimes 2025. All rights reserved.






















