Gone Spear Phishing: How Cybercriminals are Changing the Way They Work
Cyber criminals are using more targeted attacks to get around antivirus software and firewalls, using freely available information to trap people.
According to the IDC Threat Intelligence Update from February of this year, traditional forms of computer security, including antivirus software and firewalls, are only effective against 30 to 50 percent of the malware found today.
"Instead of being a massive carpet-bombing of emails, we are seeing more and more targeted attacks which are so much more difficult to stop, given that our defences today are focused on high volume and not on spear phishing," Didier Guibal, vice president at computer security firm Websense said at the launch of his company's latest suite of antivirus software.
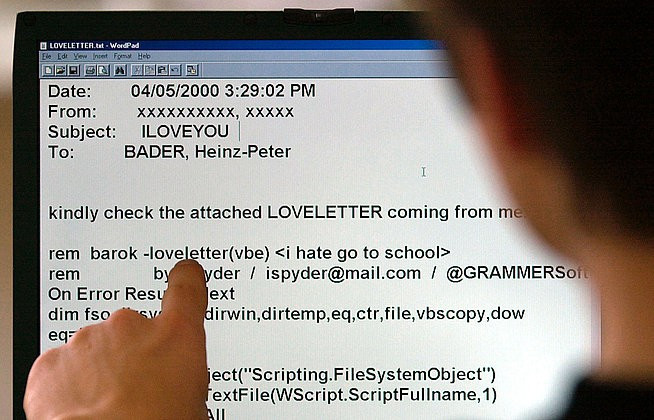
Spear phishing refers to a technique used by hackers whereby they first get a person's email address, business title and other information, before sending a tailored spam email including a link or attachment which has some malware embedded in it.
According to Guibal, 92 percent of spam contains an embedded link and the top five email spam topics are: Orders, Tickets, Delivery, Test, Tax Refund. He says they are designed to make people click on them: "People are people and they will be exposed. It is not a question of if but of when."
Traditional security is failing to protect against such targeted attacks and hackers are now proactive in trying to find ways around the latest antivirus. Guibal says that cyber criminals will go out and buy the top five signature based tools from the likes of Kaspersky and MacAfee and test their malware against the systems to see if they will work, and tweak them if they need to.
Missing Malware
Guibal revealed that according to internal testing carried out by Websense, in 2011, 641 pieces of malware went undetected by the top five signature-based anti-viruses vendors every single day of the year.
"The kind of malware that is coming after your organisations is not exposed by the tools you are using," Guibal said.
However, despite the IT professionals now realising that against the current threat traditional antivirus and firewalls are a lot less effective, this is where the vast majority of the money on IT security is being spent.
However, many companies are making it easy for cyber criminals to find out the information they need to carry out these spear phishing attacks.
Freely available informaiton
KPMG, as part of its upcoming survey, entitled Forbes 2000, looked at the websites of all companies involved in the report and downloaded around 2.5 terabytes of freely available information.
Martin Jordan, Director of Information Protection at KPMG, said this didn't involve breaking into the websites but looking at the metadata from the websites, which threw up an incredible amount of personal and sensitive information.
"Within the metadata we are taking out usernames, IP addresses, email addresses. This is all the stuff that Russian criminal gangs use when they are spear phishing your CEOs, your head of technology."
According to the as-yet-unpublished report, websites of companies offering software services are the worst culprits and the average number of usernames given up by any of these websites was 210.
Finding usernames can be as easy as is looking at who authored a particular document or press release and this could give criminals the username of the head of public relations for example. From there, they are able to target that person's machine directly because they known the head of PR will have sensitive information ahead of anyone else, which they can then sell on to interested parties.
Most websites contain a file called robots.txt. This is the first file checked by the web crawlers used by the likes of Google and Bing when they are indexing your website. The robots.txt file contains instructions for these legal web crawlers, telling them which sensitive or personal information they should ignore.
Web Crawlers
While the web crawlers from the likes of Google, Yahoo and Bing respect this agreement, there is no such agreement for web crawlers used by cyber criminals.
"A lot of developers think that [robot.txt file] is a magic bullet for hiding stuff [passwords, usernames], I don't know why they [developers] think hackers don't look in there," Jordan said. "Phishing is the route into your network at the moment."
Antivirus software is not effective these days and people are forgetting to patch internal computers, thinking that having sorted out their firewall, then everything will be alright.
Jordan showcased an example from last year of how spear phishing works. The sample case used small piece of malware code embedded in an Adobe Acrobat document, which is a typical way hackers use to spread malware, as Adobe find it hard to patch.
Working from home, the target checks his email and even though the email is titled Attack Me, the user still clicks on it and reads a message about a security threat to his system. So he downloads the Adobe document to the desktop.
When he opens the document, it sends an outgoing request to a command and control server and now the criminal is connected to the target's PC, and runs a keylogger program, designed to monitor what the user is typing.
When the user logs onto Facebook, the criminal captures his password and username. Once he gains access to the target's Facebook account, he will then start targeting his connections and depending on who the person works for or how highly ranked he is, Jordan says that information could earn a criminal up to $30,000 a day.
Access
Interested parties will pay a lot of money fro access to networks such as defence contractors or banking systems.
Jordan believes that companies need to take a number of steps in order to combat these threats. The first is to simulate attacks on your own system. This is what he and his team at KPMG do, and he says they "love doing it. Call us in and we break in."
This method means all the flaws in your system are laid bare, and makes you challenge your assumptions about how secure your systems are. Finally, Jordan says that IT managers should watch for "bad people" on their networks. "We just work on the assumption now when we go in to do assessments that everyone is infected. We see so much activity from botnets now."
© Copyright IBTimes 2025. All rights reserved.






















