ATMZombie: Malware laid the trap letting criminals steal cash from Israeli ATMs

Cybercriminals using a banking Trojan dubbed ATMZombie successfully stole hundreds of thousands in cash from unwitting customers in a complex operation that is thought to be the first successful attack to hit the banking system of Israel. Uncovered in November last year by security experts at Kaspersky Lab and now being made public for the first time, the malware uses a cocktail of phishing emails, computer trickery and real-world money mules to compromise wads of cash from targeted ATM machines.
The discovery in question, outlined by senior security researcher Ido Naor, found that hackers would first install a malicious payload on a victim's computer with the use of sophisticated social engineering tactics – essentially luring victim to download the Trojan that would conduct a 'man-in-the-middle' type infiltration to gather sensitive banking data.
Next, the malware would plant a falsified digital certificate that allowed the transfer of encrypted data between the victim's device and the banks servers. From this point on, when users connected to what they thought was the bank's secure website it would instead be a convincing page that looked identical in appearance. When the user logged in, the Trojan would steal the data and send it to the hacker's remote server.
Zombie-nation
However, the next step is what differentiates the malware from the traditional tactics deployed by banking Trojans. Instead of transferring money straight out of the account, the hackers instead recruited real people who are paid to go to actual ATMs and withdraw cash. All the mules had to do was collect the cash and then send it on to their employers, the investigators found.
"Instead of relying only on direct wire-transfer or trading credentials, [the hacker's] modus operandi started by leveraging a loophole in one of the bank's online features; and later by physically withdrawing money from the ATM, assisting money mules who are suspected to have no awareness of how the attack works − hence the Trojan was dubbed ATMZombie," explained Naor.
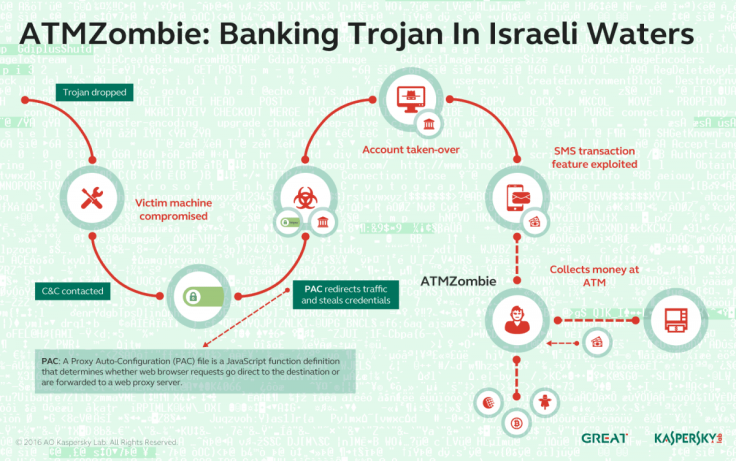
The so-called "mule" could exploit a legitimate banking feature called "SMS transaction" to withdraw money using the credentials stolen from the targeted accounts.
"[SMS transaction] has been widely used for the past few years, allowing parents, for example, to send money to kids who have no credit card, while they serve in the military or study at school. Along with a few more unique details, such as Date, Israeli ID, Name and Amount, the owner of the phone will be provided with an SMS message that authorises the cash withdraw," the researcher explained.
"The technique allowed the attackers to stay anonymous and supervise the entire campaign remotely. It also points to a new type of attack, where attackers control residents of a country to operate as an insider and deliver a basic service. This service might cause its executor to be accused of committing a crime; however, the chance of proving that they were aware of the entire operation is close to none. After all, they are not doing anything malicious."
The Kaspersky analysis found the technique was not only original but extremely well planned out. "The victim was not only lured into downloading the malware for being a client of Israeli banks, but was also targeted for being a client of a specific bank in Israel," said Naor. "This requires either very good intelligence-gathering techniques or an insider that can, legitimately or not, get a hold of the list of clients. When a list of that nature is being assembled, the hunt becomes very efficient and the attackers are able to craft each email or link to a specific victim or bank."
Following the malware attacks, which have now reportedly been curbed, all impacted customers are said to have been compensated by the banks. While Kaspersky estimates that a significant amount of money was stolen in the cyberattack, it added that swift action by the banks helped to stop the fallout from being much larger in scope.
© Copyright IBTimes 2025. All rights reserved.






















