CosmicDuke: The Latest Strand to Russia's Cyber-Espionage Campaign

A new state-sponsored malware campaign called CosmicDuke is targeting users in Ukraine and is part of Russia's on-going cyber-espionage campaign.
The new piece of malware was discovered by Finnish security firm F-Secure in April 2014 while it was analysing samples of MiniDuke - a sophisticated piece of malware which was uncovered in February 2013 targeting almost 60 government and regulatory agencies in 23 countries.
During his analysis, Timo Hirvonen from F-Secure realised that another piece of malware was using the same code. Following further analysis Hirvonen realised the piece of malware also used some code from the long-standing Cosmu family of malware, first seen in 2001.
In a technical paper released about CosmicDuke, F-Secure saying it is "the first malware seen to include code from both the notorious MiniDuke APT trojan and another longstanding threat, the information- stealing Cosmu family. When active on an infected machine, CosmicDuke will search for and harvest login details from a range of programs and forward the data to remote servers, some of which were active at the time of writing."
Ukraine and Russia
The filenames and content used in CosmicDuke's attack files to lure victims contain references to Ukraine, Poland, Turkey, and Russia.
CosmicDuke uses two attack vectors. One sees a malicious Flash exploit embedded into a PDF file which exploits a vulnerability in Adobe Reader, Adobe Acrobat or Adobe Flash when launched.
The second - more sophisticated - method uses social engineering to trick victims into opening a malicious file attached to an email.
The malicious files used in the campaign are cleverly disguised as Word documents, pictures or PDFs. The criminals behind CosmicDuke go so far as to display a document or image when the file is launched to distract victims while the malware is installed in the background.
The revelations about CosmicDuke come in the same week as it was revealed that a major state-sponsored operation called DragonFly was carrying out a sophisticated cyber-espionage campaign against thousands of companies in the US and Europe.
Soft power play
F-Secure's Sean Sullivan told Dark Reading that these DragonFly attacks were originating from Russia and speaking to IBTimes UK about CosmicDuke, Sullivan said that this discovery "fits in with the soft power that Russia has been deploying lately."
The security researcher pointed to a leaked phone conversation in February in which a US diplomat disparages the EU over its handling of the Ukraine crisis, as evidence of Russia's leveraging of cyber-espionage to attain its goals.
"These cases, with the intelligence gathering, it just seems to fit in [with Russia's strategy], like we need to know everything - not necessarily for kinetic-kaboom cyber-warfare - but we want to know everything we can about these little organisations so that we can disrupt things and tweak it here and there, just to put them off-balance, so that our real-world power play cannot be countered."
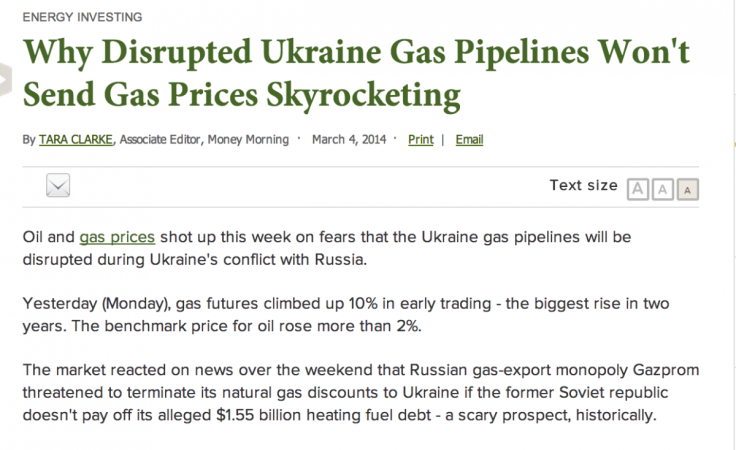
Ukraine gas crisis
Backing up this theory is the use of an image in CosmicDuke's spear phishing email campaigns related to the Ukraine gas crisis, giving an indication of both the intended victims of the malware and the nation-state which is behind the attack.
The image is a screen grab of an article titled: "Why Disrupted Ukraine Gas Pipelines Won't Send Gas Prices Skyrocketing" which was published on the Money Morning website on 4 March, 2014.
F-Secure added that the filenames and content chosen seem "to be tailored to their target's interests, though we have no further information on the identity or location of these victims yet."
© Copyright IBTimes 2025. All rights reserved.






















