'Operation Emmental' Malware Campaign Targeting Banks Across Europe

A new malware campaign believed to be the handiwork of cyber criminals based out of Russia is now targeting banks across the world, particularly those in countries like Switzerland and Austria, according to a new study.
The study carried out by security firm Trend Micro has determined that the online banking system itself bears numerous 'security holes' that can easily be exploited by cyber-criminals across the world, to steal confidential data of customers.
"Like Swiss Emmental cheese, online banking protections may be full of holes. Banks have been trying to prevent cybercrooks from accessing their customers' online accounts for ages," states Trend Micro, in a report detailing the study.
The Trend Micro report calls the latest online banking malware Operation Emmental and goes on to state that users preferring to bank online in countries like Switzerland, Austria, Japan and Sweden are comparatively more vulnerable to having their personal/confidential information stolen by hackers.
Operation Emmental is designed to bypass the generic two-factor authentication mechanism that banks employ to ensure that their customers' money remains safe.
The attacks bypass session tokens sent by a bank's remote server to users' mobile devices via text messaging. Customers preferring to bank online are required to mandatorily enter these session tokens, to start new sessions and verify/authenticate the login credentials.
The session tokens are generally sent through separate channels and are considered to be secure. However this piece of malware allows attackers to impersonate the bank, leading to confidential user login credentials being exploited.
How does Emmental steal confidential bank account data?
The Operation Emmental attacks are spread using phishing emails which masquerade as being sent from a reputed online retailer. These emails contain malware-infested links which users are prompted to click. If victims do click on the link, the malware gets downloaded to users' computers/mobile devices.
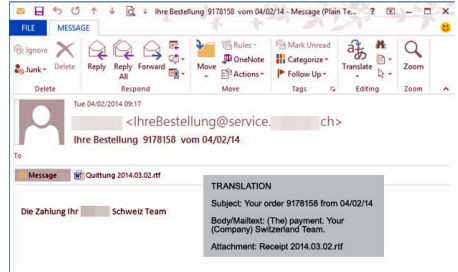
However, these computers do not get infected with malware as they might in conventional phishing attacks.
The Emmental malware manipulates the configuration of host systems, and automatically vanishes from the system, which makes it undetectable. The DNS settings of the host computer are manipulated to synchronise with an external server (operated by the cyber-criminals).
Emmental malware then loads rogue SSL root certificates within host systems. These certificates are designed to trust the external server controlled by hackers and thereby eliminate security prompts.
When users try to make online purchases (via the email posing as that from a reputed retailer) and access the bank website, they are guided towards a spoofed site that impersonates the bank's website.
After entering login credentials, users are compelled to download a malicious Android app that poses as the secure token generator. This application stops the bank's text messages and redirects these to a rogue server/phone number operated by hackers.
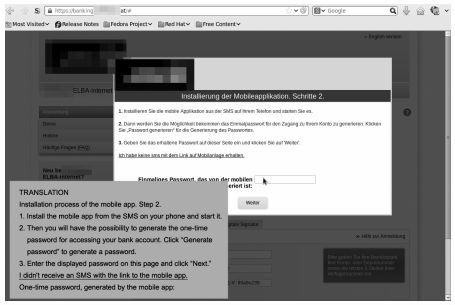
This attack leads to hackers gaining unauthorised control of users' bank account details via both the phising scam and the spoofed secure tokens that users assume to be from their bank.
Are banks at fault for not providing security to customers?
The study also reports that various banks themselves were found to be at fault, for not implementing secure authentication mechanisms for their customers.
"Some of the banks we looked into do not exclusively use this system," said the report. "However, the fact remains that banks let most of their customers use session tokens with the aid of SMS and leave more secure methods for premium clients only or as an alternative option, possibly due to increased operating costs and ease of use."
Trend Micro said it was able to trace the operators of the malware back to online nicknames: -=FreeMan=- and Northwinds, who have been active since 2011. Back then, they spread off-the-shelf malware like SpyEye and Hermes.
"Further investigation revealed that every time users of infected machines tried to access six bank domains in Austria, seven in Sweden, 16 in Switzerland, and five in Japan, they would be directed to a malicious server instead."
With the latest attack targeting Swiss banks (along with banks in other European countries), it is now imperative that banks realise the dangers of such an attack, and warn customers not to click on malicious links in emails.
Banks should also ensure that enhanced two-factor authentication is provided to all customers regardless of customers' financial status.
© Copyright IBTimes 2025. All rights reserved.





















