OpenSSL Vulnerable to Two New Attacks Months After HeartBleed Bug Revealed
It has not been a good week for open source encryption protocol OpenSSL, with first a new way of exploiting the Heartbleed Bug discovered, and now a entirely new flaw within the code leaving millions of Android smartphones and tablets at risk.
On Thursday, the OpenSSL Foundation confirmed that it had been informed of a new flaw in the code.
Researcher Masashi Kikuchi of Japanese security firm Lepidum highlighted the vulnerability which allows for man-in-the-middle (MITM) attacks, meaning hackers could intercept and decrypt traffic being sent between vulnerable clients (smartphones, laptops, tablets) and servers.
To exploit the new flaw a hacker would need to be in position on the network to intercept the traffic and they could only decrypt traffic between a vulnerable client and vulnerable server - limiting the situations where this flaw could be used.
However one of the most obvious ways this new exploit could be used is on open wireless networks, which are widespread these days. OpenSSL isn't used in many client devices, but the Android mobile operating system does use it meaning hundreds of millions of smartphones and tablets are at risk.
The vulnerable piece of code which lead to the Heartbleed Bug was in the OpenSSL code since 2011 but according to the Foundation the latest flaw has been present in the code for 16 years, dating back to 1998.
Meet Cupid: Heartbleed 2.0
As I said, this has not been a good week for OpenSSL.
Two months after the Heartbleed Bug was first made public, a security researcher has discovered a new way of exploiting the flaw in OpenSSL which can steal information from wireless networks and the devices which connect to them.
The Heartbleed Bug made headlines a couple of months ago when it was revealed that millions of websites were vulnerable to a flaw in the OpenSSL code which they used to encrypt their communications, meaning hackers could potentially steal millions of usernames, passwords and credit card numbers.
Dubbed the Heartbleed Bug, system administrators were urged to update their systems as a matter of urgency, but now a Portuguese security researcher has discovered a new way of exploiting the vulnerability.
Luis Grangeia has published a new piece of software which he has dubbed Cupid which gives those looking to attack vulnerable systems the ability to easily steal passwords, usernames and other sensitive informations from routers and devices connected to them as long as they relied on vulnerable versions of OpenSSL.
Businesses beware
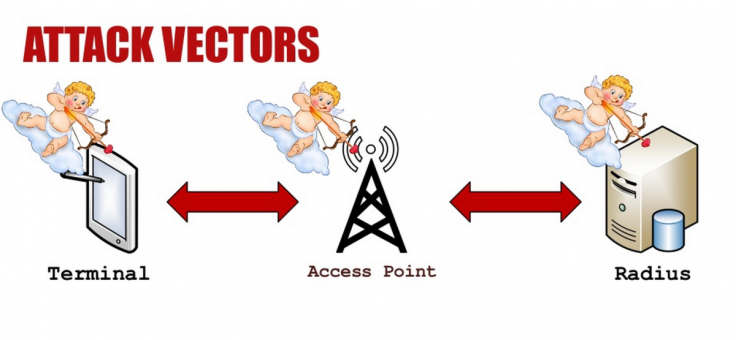
The code comes in the form of two extensions. The first allows a hacker to create a malicious Wi-Fi network and steal information from any devices which connects to it. The second works in the opposite way, and if applied to the client side (laptop, tablet, smartphone) would allow anyone to steal information from a vulnerable wireless network they connected to.
In the second case, the exploit only works on certain types of wireless network which are secured using the extended authentication protocol (EAP), which many large organisations use to password-protect access.
In a blog post explaining his research, Grangeia said: "This is basically the same attack as Heartbleed, based on a malicious heartbeat packet. Like the original attack, which happens on regular TLS connections over TCP, both clients and servers can be exploited and memory can be read off processes on both ends of the connection. The difference in this scenario is that the TLS connection is being made over EAP, which is an authentication framework/mechanism used in wireless networks."
© Copyright IBTimes 2025. All rights reserved.






















