Syrian Electronic Army Continues Cyber Campaign with CNN Hack
The Syrian Electronic Army are proving to be one of the most consistently effective hacker groups in operation, as they claimed their latest victim this week breaching the social media accounts and blogs of US broadcaster CNN.
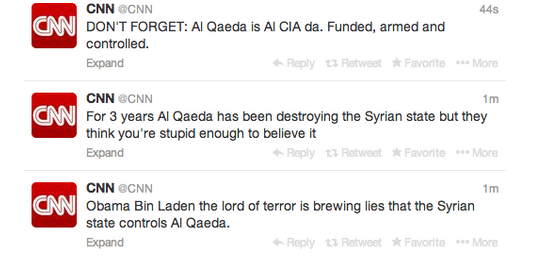
On Thursday evening the Syrian Electronic Army (SEA), the cyber wing of Syrian president Bashar al-Assad, took control of CNN's main Twitter account and posted messages related to the conflict in the Middle Eastern company.
The SEA claimed that US president Barack Obama "the lord of terror" has been spreading lies about the Syrian state being in control of al-Qaida adding that the terrorist group has been "destroying the Syrian state" for three years.
Situation Room
It appears the SEA was able to compromise CNN's Hootsuite account, a piece of software used to manage multiple social media accounts. Images leaked to journalist Matthew Keys also show that the SEA was able to briefly compromise the Wordpress account of the broadcaster which is used to publish blogs on the site such as The Situation Room and Political Ticker.
The main CNN Facebook account and the CNN Politics' Facebook account were also compromised.
The posts were deleted within minutes according to CNN and the accounts are back under its control.
Phishing campaigns
The SEA rose to prominence in 2013 with high profile attacks against western media outlets, including Sky News, the BBC and the Guardian. It's most high-profile attack came when it hacked of the AP Twitter feed which saw $140 billion wiped off the S&P 500 index for a brief period.
The group of hackers is able to compromise these accounts by utilising phishing campaigns where they sends emails to multiple people working at the media company, needing just one email account associated with the social media accounts to be compromised.
This email address is then used to send messages to other employees within the newsroom asking them to sign in to what looks like a login site for the company's webmail.
The credentials entered are then used to access various accounts associated with the target company.
Little is known for certain about its origins or the number of people involved in the group and while it insists it has no official links to the Assad regime, it is widely thought that the group receives financial and logistical support from the Syrian government.
© Copyright IBTimes 2025. All rights reserved.






















