Won't pay? No problem, Cerber ransomware adds your PC to a botnet to send out DDoS attacks

For the first time ever, cybersecurity researchers are seeing instances where ransomware is being bundled together with bots in order to turn computers into zombies that can send malicious Distributed Denial of Service (DDoS) attacks.
Ransomware is a type of malware that holds a large collection of data hostage on a victim's computer, including important documents, photos and videos. Once installed, the victim is shown a user interface explaining that the files will be destroyed unless the victim pays a bitcoin ransom to the hackers.
The latest incarnations of ransomware come so meticulously coded with strong cryptography that it is difficult to find a way around it, so many companies and victims prefer to pay up rather than lose valuable files, but the international cybersecurity community is constantly developing ways to decrypt malware and generally advises victims not to pay.
So if victims are refusing to pay to decrypt their files, cybercriminals have found another way to make trouble. According to researchers from enterprise security software firm Invincea, attackers have modified the existing Cerber ransomware so now, not only does it hold a victim's files and PC hostage, but the new malware variant also quietly starts sending out a huge amount of network traffic from the infected PC.
From Russia with love
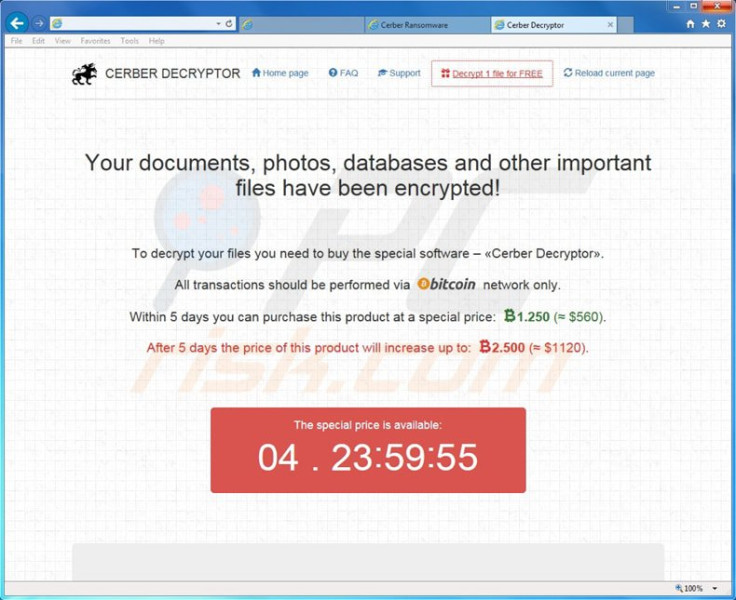
Cerber originates from Russia and even without the DDoS bot, it is pretty terrifying as it comes with a text-to-speech function that will literally read you the demands of the cybercriminal out loud, demanding 1.24 bitcoins ($550, £380) in ransom to unlock the files.
At the moment, there is no way to decrypt the files without paying the ransom, and it is believed that Cerber is being touted as a "Ransomware-as-a-Service"-type of product where criminals deploy the ransomware, and pay a percentage of the ransom fee back to its developers.
Similar to other ransomware, Cerber spreads by malicious .RTF word document files sent via email phishing campaigns, and once opened, the file executes a malicious VBscript that downloads and runs the malware to hijack the user's computer.
The only silver lining is that the ransomware variant analysed by Invincea can be easily detected by many top antivirus software, and a scan by VirusTotal shows that 37 out of 57 antivirus programmes were able to block it from being activated.
"'The observed malware seems to serve multiple purposes. First, it is a typical ransomware binary that encrypts the user's file system and files while displaying a ransom note. Second, the binary could also be used to carry out a DDoS attack," Invincea researcher Ikenna Dike writes in a blog post.
"The observed network traffic looks to be flooding the subnet with UDP packets over port 6892. By spoofing the source address, the host could direct all response traffic from the subnet to a targeted host, causing the host to be unresponsive."
© Copyright IBTimes 2025. All rights reserved.






















