First File-Encrypting Ransomware Targeting Android Smartphones Discovered

A security company has discovered the first example of file-encrypting ransomware specifically targeting Android smartphones.
While there have been a number of examples of ransomware discovered on Android previously, security firm Eset claim this is the first one which encrypts files on your smartphone and refuses to unlock them unless you pay a ransom.
Eset says it discovered the ransomware within an app called Sex Xionix, which is currently not available on the Google Play store.
Once the ransomware - which Eset detects as Android/Simplocker - is downloaded onto an Android smartphone or tablet, it scans the SD card for certain file types (images, videos, documents), encrypts them using AES, and demands a ransom in order to decrypt the files.
The malware will also contact a command-and-control server sending identifying information about the device, including the phone's IMEI number, with the server being hosted on the Tor network to hide its location.
Russian
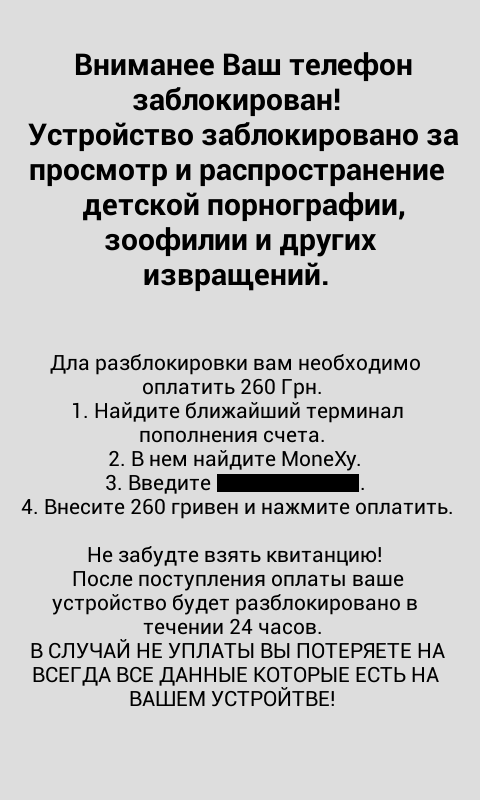
The version of the ransomware which Eset has discovered throws up a ransom message which is written in Russian (see image below), with the payment demanded in Ukrainian hryvnias, which mean the criminals behind Simplocker are targeting this region.
The message reads:
WARNING your phone is locked!
The device is locked for viewing and distribution child pornography , zoophilia and other perversions.
To unlock you need to pay 260 UAH.
- Locate the nearest payment kiosk.
- Select MoneXy
- Enter {REDACTED}.
- Make deposit of 260 Hryvnia, and then press pay.
Do not forget to take a receipt!
After payment your device will be unlocked within 24 hours.
In case of no PAYMENT YOU WILL LOSE ALL DATA ON your device!
The ransom demanded in this version of 260 Hryvnia is equivalent to just over £13, which is a fraction of the amount typically demanded by ransomware on PCs.
Do not pay up
In a blog post describing Simplocker, Eset said:
"While the malware does contain functionality to decrypt the files, we strongly recommend against paying up – not only because that will only motivate other malware authors to continue these kinds of filthy operations, but also because there is no guarantee that the crook will keep their part of the deal and actually decrypt them."
Last month we reported on a piece of police ransomware which was discovered by security researcher Kafine which was related to the pernicious Cryptolocker ransomware which has gained a lot of attention in late 2013. However Eset says it was not related to Cryptolocker nor did it encrypt files on your smartphone unlike Simplocker.
Eset believes Simplocker in its current form is a proof-of-concept or work-in-progress, as the implementation of the encryption doesn't come close to matching that used by Cryptolocker.
© Copyright IBTimes 2025. All rights reserved.






















