How Banks and Customers Can Tackle Gameover Zeus and Cryptolocker Viruses

This week, a lot of attention has been focused on the crackdown of the criminal gangs behind the GameOver Zeus and CryptoLocker viruses, but for many it is too late as there are already hundreds of thousands of machines infected.
We've been told that losses are estimated at up to $100m (£60m, €73m), but this could jump dramatically as malware lays in wait ready for its next attack.
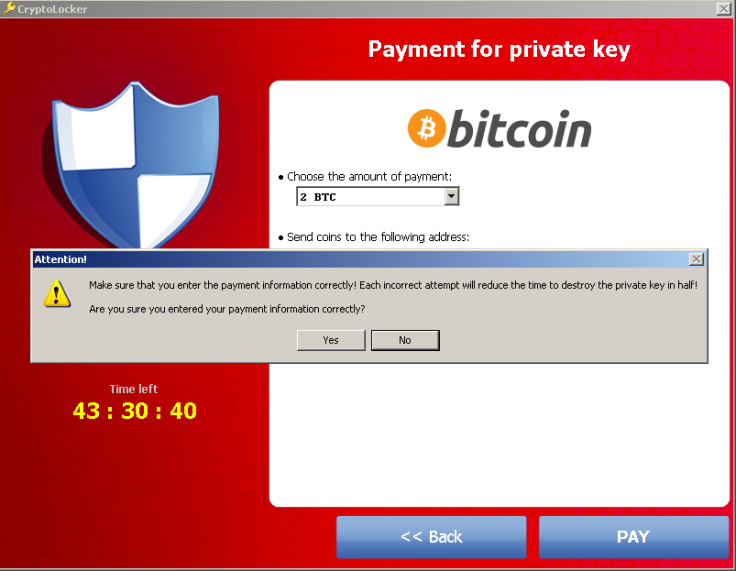
Gameover Zeus is a botnet, which was designed to steal banking and other credentials from computers it infected, typically via a link or attachment in an email. However, in the event that the infected computer is not able to give a significant financial reward, it gets help from another type of malware called Cryptolocker.
Instead of stealing financial data, it encrypts all the files on the infected machine and demands a ransom of one bitcoin (roughly around £300-£400).
Global Coordination
The scale of the co-ordination between the National Crime Agency (NCA) and the FBI to stop this one attack is unprecedented, but we need to remember that cyber criminals are always evolving and looking for their next way to exploit the system.
With such huge cost implications, banks need to remain vigilant in their detection and prevention schemes for dealing with irregular activity emanating from compromised machines.
It sounds simple, but techniques such as monitoring for new payees, random faster payments, CHAPS or wire requests, and even online purchases that are not part of the normal transaction behaviour of a customer, can be crucial to stopping criminal activity.
Currently banks use a variety of layered detection and challenge response techniques to help identify any abnormal activity. But some of these techniques can impact the customer experience, meaning it is a tricky balance for banks to get right to avoid frustrating their customers.
There is no one solution that each bank uses, but most banks will include the use of one time passcodes when logging onto the internet banking applications or when making payments to new payees.
One time passcodes are generated from a variety of different methods including security tokens supplied to customers at enrolment, via SMS messages, or simply the use of a card authentication device – customers simply insert their card into the device, enter their 4 digit pin and the device gives them a unique code.
Beating the Bot
There are banks that do utilise more stealth-like types of technologies including software that establishes a secure link between the bank and the customer's device.
There are other banks that go a step further, capturing details of the device, language and operating system a customer is using to initiate the payment from. This data can then be held to form a DNA fingerprint that banks can use to check current activity. Where anomalies are identified, the payment could be declined or customer subjected to stronger authentication and verification processes before the payment is made.
But it isn't just banks that are responsible for keeping our money secure.
For consumers, it is essential to keep an eye on your accounts and flag to the bank any activity that appears abnormal and immediately report transactions not made by you.
It sounds simple, but keeping your anti-virus, software and operating systems up-to-date will help add that extra level of protection – many businesses are still using Windows XP, which has been without security support since April this year.
Cyber criminals are becoming more adept and sophisticated and are increasingly using social engineering techniques to manipulate and exploit consumers in to giving away their confidential information.
Criminals are also able to easily harvest data from social media channels that we make freely available to onlookers.
Making sure that our bank accounts are not wiped clean by criminals is simply the responsibility of all of us. Banks need to be sure that they are doing everything possible to avoid criminals stealing the money of their customers, while customers need to be better equipped to deal with criminals lurking all over the world trying to gain access to your personal detail.
Remember always to make sure you know who is sending you the email, and when in doubt, don't click the link.
Andy Morris, is the solutions lead at ACI Worldwide, a US-based electronic payment systems company for financial institutions and retailers.
© Copyright IBTimes 2025. All rights reserved.




















