36 fake security apps harvesting user data and tracking their location found in Google Play Store
These apps were able to collect a slew of user and device information and send it to a remote server.

Security researchers have unearthed 36 malicious Android apps parading as security tools on the Google Play Store that actually harvest user data, track their location and more. According to Trend Micro, these apps offered users a wide range of security capabilities including cleaning junk, saving battery, scanning, CPU cooling, locking apps, Wi-Fi security, message security and more.
Going by the names Security Defender, Guardian Antivirus, Smart Security, Security Keeper, Deep Cleaner, and Advanced Boost among others, the applications did actually perform these tasks. However, they also aggressively bombarded users with advertisements, secretly collected user data and even tracked user location.
Researchers said the apps, once launched, would not actually appear on the device launcher's list of applications nor would their shortcuts pop up on the phone's screen.
Trend Micro noted that the malware's "hide" function was explicitly designed not to run on specific devices including Google Nexus 6P, LGE LG-H525n, Xiaomi MI 4LTE and ZTE N958St.
It is possible the malware developers knew that this tactic would not work on these devices, or they wanted to avoid being checked by Google Play during inspection periods.
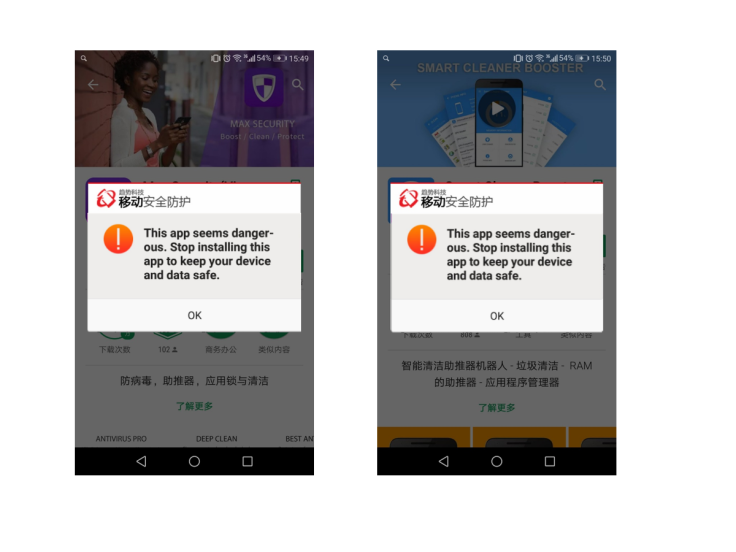
For other devices, these hidden apps would simply push alarming fake security notifications, warnings and pop-up windows to the user.
"For example, if the user installs another app, then it will immediately be reported as suspicious. Or the user will be sent notifications like '10.0 GB files are being wasted,' which will prompt some kind of action," the researchers wrote. "But the data shown in these messages are fake — they are just used to add a layer of legitimacy to the app."
The researchers noted that the developers behind the malware made an effort to make their false notifications believable and ward off the suspicions of users.
For example, if a user clicked on a button to "resolve" a fake security issue such as a detected "Fraud SMS Broadcast Vulnerability", an animation would then pop up to illustrate to the user that the problem has been "resolved".
Besides the fake security alerts, users were also hit with a trove of advertisements on nearly every action they performed.
"The aggressive ads show up during many different scenarios — for example, after the app sends notices to unlock the device screen or if the user is told to connect to a charger," Trend Micro said. "The user is bombarded with ads with almost every action. It is clear that one of the main focuses of the app is ad display and click fraud."
Users are also asked to sign and agreed to an end-user licence agreement (EULA) that describes the information that will be gathered and used by the app. However, the researchers said that the app abuses privacy since "the collection and transmission of personal data is unrelated to the functionality of the app".
These apps were able to collect a slew of user and device information and send it to a remote server. This included user's Android ID, Mac address, IMSI, details about the OS, model and brand of the device, language, location information, data on other installed apps like Facebook and Google Play and even device specifics such as screen size.
Trend Micro spotted the apps in December 2017 and has notified Google of the fake apps. They have since been removed from Google Play.





















