FBI using information from Anonymous hacktivist to help find Centcom hackers
In a strange turn of events, the FBI is using information obtained by hacktivist group Anonymous to help it find the hackers who compromised the Centcom Twitter and YouTube accounts.
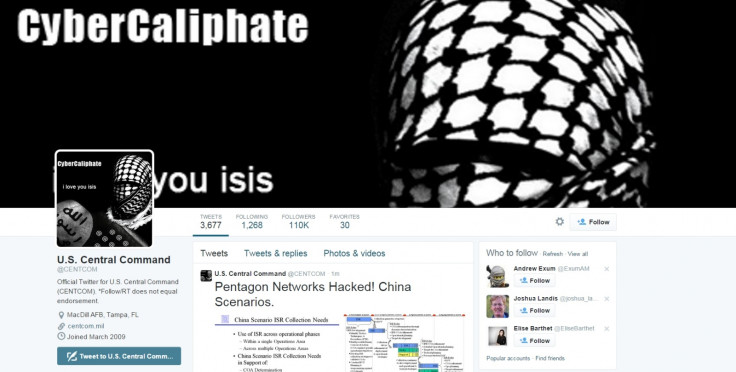
Last week, just as President Barack Obama was outlining new cyber-security measures, the Twitter account and YouTube channel of US Central Command (Centcom) was compromised for 40 minutes and defaced with pro-Islamic State (IS) messages and threats against US soldiers.
The defaced Twitter account named CyberCaliphate - the hacking wing of IS - as the group behind the attack, but there was at least one voice suggesting that the attacks may not have come from the Middle East.
Soon after the attack, the person behind the Anonymous-related Twitter account @TheAnonMessage claimed to have information that the attacks on the social media accounts came from inside the US - from the state of Maryland.
The account listed 11 IP addresses it claimed were used in the attacks, adding that it didn't appear that the attackers were using proxies to try and hide their real location.
Working together
The @TheAnonMessage even cheekily tweeted to the official FBI Twitter account to inform them of the information they had obtained, adding "You're welcome".
We've traced the hacker who infiltrated @CENTCOM to somewhere in the State of Maryland. @FBI, you're welcome.
— TheAnonMessage (@TheAnonMessage) January 12, 2015And it appears as if the FBI has taken notice.
According to a memo seen by security researcher Pierluigi Paganini, the FBI forwarded the IP address information to several security experts hoping to verify the reliability of the information with the help of the data that is in possession of the experts. The memo reads:
On 12 January 2015, at 2:01PM CST, @TheAnonMessage, a Twitter account associated with the Anonymous hacking group, tweeted 11 IP addresses involved with the CENTCOM hack with the message. The FBI is providing a list of IPs obtained from @TheAnonMessage Twitter Account, and encourages recipients to examine their networks for any activity related to these IP addresses.
This is likely a first for FBI-Anonymous relations, with the agency and the hacktivists typically at opposite ends of the spectrum when it comes to cyber-security affairs.
The use of information gathered by @TheAnonMessage is all the more intriguing when you realise that this was the account which erroneously identified a police officer as the killer of Mike Brown in the wake of the shooting dead of the unarmed teenager in Ferguson in August, 2014.
The account subsequently suggested it deliberately named the wrong person to force the police to reveal Darren Wilson's identity.
The FBI has in the past tracked, arrested and imprisoned multiple members of the hacktivist group, including most famously Barrett Brown and Jeremy Hammond in the US, as well as several members of the LulzSec offshoot in the UK.
The FBI has of course worked with Anonymous members in the past though only having first threatened them with jail. This was the case with Sabu, aka Hector Monsegur, who was a leading light in Anonymous until June 2012 when he became an informant and helped identify many of his former colleagues - before walking free for his "extraordinary cooperation".
© Copyright IBTimes 2025. All rights reserved.






















