'First ever' malware-as-a-service for Apple Macs discovered on dark web
'MacRansom' and 'MacSpy' being sold 'as a service' on the dark web, experts warn.

Two separate malware-as-a-service websites catering to cybercriminals lacking the expertise to create their own computer exploits have appeared on the dark web, claiming to offer "sophisticated" strains of ransomware and spyware which can easily infect Apple's Mac computers.
Researchers from cybersecurity firms AlienVault and Fortinet were able to obtain samples of the malicious code by posing as potential buyers. The underground portals peddling the illicit services have been online since late-May this year, according to Bleeping Computer.
The variants, dubbed "MacRansom" and "MacSpy", are currently being advertised on two hidden websites which appear almost identical in design.
Both research teams indicated it could be the first time such a "malware-as-a-service" targeting Mac OS has hit the dark web. Traditionally, Microsoft's Windows had been the primary target.
The malware strains, analysis showed, were not available to download directly from the websites and were often patched together from known code.
Instead, potential buyers had to contact the developer with specific requests. The researchers said this suggested the service was a massive scam. But, to their surprise, the developer responded.
MacRansom
In an frequently-asked-questions page for MacRansom, published by Fortinet, the culprit said the ransomware was aimed at "people who want to covertly retaliate another Mac user (sic)" and "people who want to earn easy money from unsuspecting family members, friends, colleagues and classmates."
The developer said each exploit would be assigned its own unique bitcoin address. Once payment from a victim comes in, he or she promise to send 70% of the money to the bitcoin address and keep the remaining 30% as profit. It is unclear if any real customers exist.
Typically, ransomware-as-a-service (RaaS) makes it easier for less tech-savvy cybercriminals to launch attacks. If successfully, the developer and the criminal share the profit.
Fortinet's Rommel Joven and Wayne Chin Yick Low, who published a blog post on their findings, said analysis showed the ransomware could only encrypt a maximum of 128 files. As standard, it demanded 0.25 bitcoin (£560; $700) and asked the victim to contact getwindows@protonmail.com.
"This piece of crypto-ransomware is not as sophisticated as other OSX crypto-ransomware that have been previously disclosed," the pair wrote, adding that evidence suggested in some cases full decryption may not even be possible due to the way the strain was coded.
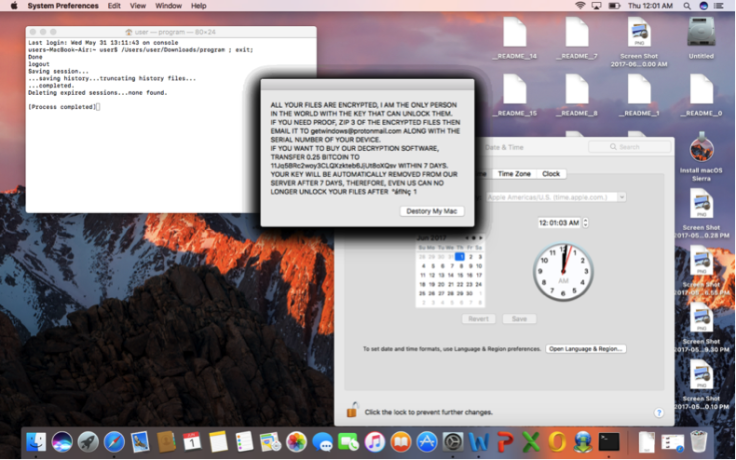
"It is not every day that we see new ransomware specifically targeting Mac OS platform," the blog continued.
"Even if it is far inferior from most current ransomware targeting Windows, it doesn't fail to encrypt victim's files or prevent access to important files, thereby causing real damage."
Running a MacRansom sample, the researchers said a prompt appeared letting users know it was from an unidentified source. "As long as users don't open suspicious files from unknown developers, they are safe," they said.
"Clicking open gives permission for the ransomware to run."
MacSpy
Advertised as the "most sophisticated Mac spyware ever", MacSpy boasted features including invisibility, voice recording, key logging, iCloud syncing, screen-captures and browser data storing. "Once installed, there will be no digital trace that can be associated with you," it claimed.
Those behind MacSpy teased an "advanced" version which could be bought with cryptocurrency. It claimed to enable "retrieval of any files and data from the Mac", "ability to adjust capture and recording intervals remotely" and "encryption of entire user directory in a few seconds."
AlienVault's research team concluded this form of Mac-based malware was "not as polished" as other known strains currently in the wild.
AlienVault researcher Peter Ewane said in a blog post: "In order to receive a copy of MacSpy we had to email the author our preferred username and password, in order for them to make us an account. After confirming our details they [...] delivered a zipped file and [...] instructions."
"People generally assume when they are using Macs they are relatively safe from malware," he added. "This has been a generally true statement, but this belief is becoming less and less true by the day, as evidenced by the increasing diversity in Mac malware along with this name family.
"While this piece of Mac malware may not be the stealthiest program, it is feature rich and it goes to show that as OSX continues to grow in market share. we can expect malware authors to invest greater amounts of time in producing malware for this platform."
Apple did not immediately respond to request for comment.

While the majority of malware, ransomware and Trojans still targets Microsoft Windows, Apple devices are increasingly being targeted by cybercriminals.
"There is Mac malware and, unfortunately, even though there's a small quantity the quality and nature of it pretty much copies what's happening on Windows," Sophos' Paul Ducklin said in a demonstration during the Infosecurity Europe conference last week.
"Whatever has worked on Windows, that kind of malware can be written for the Mac," he continued. "We think the crooks maybe haven't really figured out how to monetise it on the Mac yet, or maybe they don't really need to because they are making so much money off Windows.
"But there are plenty of them who are trying."
© Copyright IBTimes 2025. All rights reserved.






















