Hackers target Ukrainian software company to spread the notorious Zeus banking trojan
Researchers said the attack occurred in August 2017, around the time of Ukraine's Independence Day holiday.

Hackers have compromised the official website of Ukrainian accounting software developer Crystal Finance Millennium to distribute a new variant of the malicious Zeus banking trojan. According to Cisco Talos researchers, the company's website was found dispersing malware that was retrieved by malware downloaders attached to messages as part of an ongoing spam campaign.
Researchers said the attack occurred in August 2017 around the time of Ukraine's Independence Day holiday. Ukrainian authorities and businesses were alerted to the cyberattack by local security firm ISSP.
However, researchers noted that the hackers did not compromise the company's update servers or have the same level of access observed in the earlier Nyetya compromise.
In this attack, malicious malware-laden emails were sent out featuring a ZIP archive that contained a JavaScript file that functioned as a malware downloader. Once opened, the Javascript is executed and causes the system to retrieve the malware payload, run it and infect the system with a variant of the Zeus banking trojan.
One of the domains used to host the malware was associated with CFM's website, researchers noted. The site has also been observed distributing the PSCrypt ransomware, an aggressive strain of malware that heavily targeted Ukrainian users last year.
Since the source code for version 2.0.8.9 of the ZeuS trojan was leaked in 2011, other threat actors have taken inspiration from the malicious code and incorporated it in multiple other banking trojans.
"Talos was able to identify significant code reuse between the malware being distributed by this campaign and the leaked version of the ZeuS source code," researchers said. "Once executed on systems, the malware performs several actions to determine whether it is being executed in a virtualized sandbox environment.
"In cases where the malware does not detect it is operating in a sandbox environment, it then takes steps to achieve persistence on infected systems."
The malware even creates a registry entry on an infected system to make sure the malicious code is executed every time the compromised device is restarted.
Once the system is infected, the malware tries to reach out to different command and control (C&C) servers.
"When Talos began researching the threat we found that one of the domains was already being sinkholed, one was being controlled by the bad actors, and the third was not yet registered," researchers said.
Most systems infected by the malware were located in Ukraine and the United States, researchers found. The most heavily affected ISP was that of PJSC Ukrtelecom - the company governed by Ukraine's Ministry of Transportation and Communications.
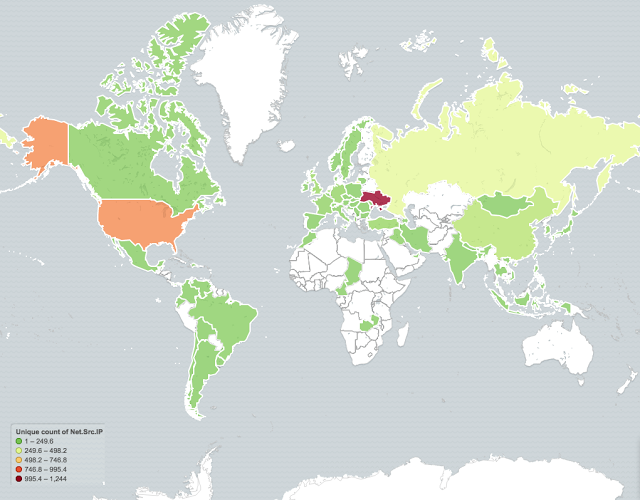
"In total, our sinkhole logged 11,925,626 beacons from 3,165 unique IP addresses, which demonstrates the size of the spread of this particular malware," researchers said.
"As we saw repeatedly throughout 2017, attackers are increasingly attempting to abuse the trust relationship between organizations and their trusted software manufacturers as a means of obtaining a foothold within the environments they are targeting. As organizations deploy more effective security controls to protect their network environments attackers are continuing to refine their methodologies."





















