Mumsnet hackers publish 3,000 passwords and call armed police to CEO Justine Roberts' house
A hacking collective who took responsibility for launching a cyberattack on the Mumsnet parenting website and sending armed police to its owner's house has published a database claimed to contain 3,000 user passwords. The group, called Dad Security, published a list which appears to show the user names, IP addresses and passwords of the users, plus the email addresses and passwords of site administrators.
The website and its forums were attacked on 11 August when they were knocked offline for several hours; at least 11 user accounts were compromised. Simultaneously, Mumsnet founder Justine Roberts was 'swatted' in an incident where armed police were wrongly called to her London home.
The attack began with a DDoS (distributed denial of service) attack on the website. Common among online hacking collectives, this attack bombards a website with traffic until it is knocked offline. The site was restored by 10am the next morning, 12 August.

In the aftermath it was found that at least 11 user accounts were compromised; this is thought to have been through phishing attacks, however. Roberts said on 19 August that no data was stolen during the DDoS attack.
All 7.7 million Mumsnet users have now been forced to change their passwords, Roberts says, and are reminded to change them regularly to avoid being caught up in a phishing attack. Phishing is done by sending an email posing as a website's login page to the victim, who then enters their details, which are sent to the attacker and used to log in. Roberts says all passwords have now been reset.
Swatting
Hours after the attack began, an armed response team from the Metropolitan Police arrived at Roberts' house in Islington, North London, following reports of a gunman prowling the local area and gunshots being heard. This was revealed to be an act of swatting, where a fake distress call is made with the intention to get armed police to the victim's house. A second incident saw armed police arrive at the house of someone who interacted with Dad Security over Twitter.
Posting on Mumsnet, Roberts said: "An armed response team turned up at my house last week in the middle of the night, after reports of a gunman prowling around. A Mumsnet user who engaged with @DadSecurity on Twitter was warned to 'prepare to be swatted by the best' in a tweet... after which police arrived at her house late at night following a report of gunshots. Needless to say, she and her young family were pretty shaken up. It's worth saying that we don't believe these addresses were gained directly from any Mumsnet hack, as we don't collect addresses. The police are investigating both instances."
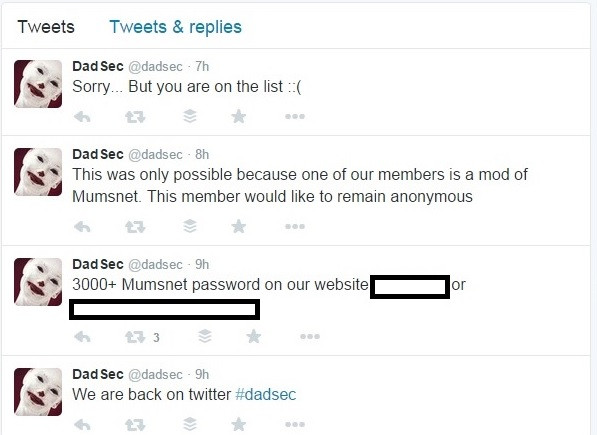
Dad Security: 'One of our members is a moderator of Mumsnet'
The @DadSecurity Twitter account, which has now been suspended, claimed to have access to Mumsnet user data and, later on 12 August, Roberts recalls: "It become apparent that someone/ones had hacked into some of Mumsnet's administrative functions, at which point they were able to redirect our homepage to the @DadSecurity Twitter profile page, as well as to edit posts from two users' accounts and a [Mumsnet HQ] account on our forums."
On 19 August a new Twitter account, called @DadSec, was created and posted a link to what it claimed to be 3,000 user accounts and their passwords. It isn't clear if these passwords have since been reset by Mumsnet. The account tweeted: "This was only possible because one of our members is a mod of Mumsnet. This member would like to remain anonymous."
In a series of tweets the account said: "This is only the start...it is not over yet...we have more planned." The account follows just two others, both related to campaign groups Fathers4Justice.
However, a spokesperson told IBTimes UK: "Fathers4Justice can confirm that they have no connection or contact with this group and unreservedly condemn these actions which have no place in a movement campaigning for loving fathers who are struggling to see their children."
IBTimes UK has confirmed that a selection of the 3,037 user names listed are those of Mumsnet users. Roberts says she is sure that the hackers are unable to access user passwords "because [Mumsnet] doesn't hold them as plain text; they're all encrypted, so that no one - not even us - can see them."
She says her "best guess at this stage" is that the accounts were compromised through phishing, adding: "We are looking into what we can do to strengthen our defences against phishing, but in the meantime we need to ask you to be vigilant."
IBTimes UK has contacted Mumsnet users who appear on the list of claimed passwords, and Dad Security for a comment, and will update this article when we get a reply. Mumsnet has said it will be in touch "as quickly as possible".
More from the technology desk
© Copyright IBTimes 2025. All rights reserved.






















