Surgical robots hacked by researchers to alter commands and disrupt functions

Security vulnerabilities in surgical robots have been exposed by researchers, who hacked next generation systems to prove that they could be hijacked remotely.
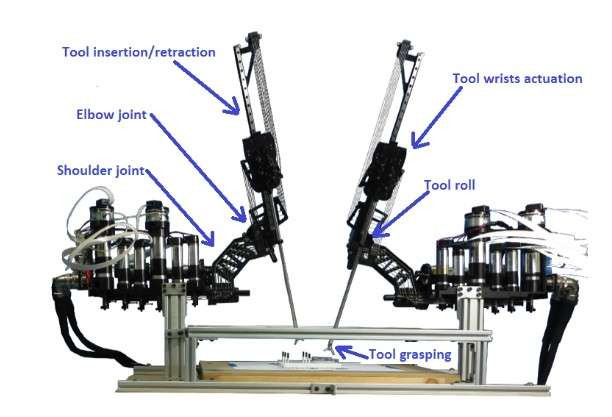
Researchers from the University of Washington (UW) carried out a series of cyberattacks on teleoperated (remotely operated) surgical robots using non-private networks.
Various attack techniques were utilised, including a denial-of-service (DoS) attack that overloaded the robot with useless data and made it difficult to operate.
A "man in the middle" attack succeeded in altering the commands sent from the operator to the robot, disrupting a wide range of the machine's functions.
"We want to make the next generation of telerobots resilient to some of the threats we've detected without putting an operator or patient or any other person in the physical world in danger," said UW doctoral candidate and the paper's lead author Tamara Bonaci.
$20bn industry
A recent report into the surgical robots market predicted that it would be worth $20bn (£13bn) within the next six years.
Next generation systems are expected to improve traditional open surgery and ensure better outcomes for patients.
According to the Radiant Insights report, "patients fare better when the surgery is done by surgical robots", however it does not take into account the risk of cyber attacks or patient acceptance.
The attacks carried out by the UW researchers will raise questions about the proliferation of surgical robots being used for clinical use in procedures such as tumour removal and heart valve repair.
Robots approved by the US Food and Drug Administration (FDA) for these procedures use a different communication channel to the one used by the researchers, however secure networks are not an option in certain locations.
"If there's been a disaster, the network has probably been damaged too," said Howard Chizeck, professor of electrical engineering and co-director of the UW BioRobotics Lab. "So you might have to fly a drone and put a router on it and send signals up to it.
"In an ideal world, you'd always have a private network and everything could be controlled, but that's not always going to be the case. We need to design for and test additional security measures now, before the next generation of telerobots are deployed."
© Copyright IBTimes 2025. All rights reserved.






















