Uh oh – TeslaCrypt PC ransomware is now impossible to crack, so you're going to have to pay up

We've got bad news guys – remember that pesky PC ransomware TeslaCrypt? Security researchers say the latest incarnation of the pesky malware cannot be defused, meaning the only way for victims to get their files back will be to pay up.
Ransomware is a particularly nasty type of malware that holds a large collection of data on a victim's computer hostage, including important documents, photos and videos. Once installed, the victim is shown a user interface explaining that the files will be destroyed unless the victim pays a bitcoin ransom to the hackers.
The ransomware is typically distributed via email phishing campaigns, where victims are tricked into downloading a malicious attachment, although recently victims are being tricked into clicking on malicious ads on popular websites.
There have been reports of ransomware since 2013, and in one case a police department paid the ransom rather than lose crucial evidence pertaining to a case, and in the past, researchers also found that some of the ransomware acted as an empty threat, and nothing happened if the ransom wasn't paid.
However, the most recent examples of ransomware are so meticulously coded with strong cryptography that it is difficult to find a way around it, and now the FBI is warning that the same technology can be used to hijack an entire company's network of computers, rather than just one machine.
In particular, TeslaCrypt focuses on searching and encrypting all file extensions relating to 40 popular computer games that might be stored on the victim's PC, as well as encrypting Word, PDF and JPEG files.
TeslaCrypt 3 is one of the most advanced ransomwares today
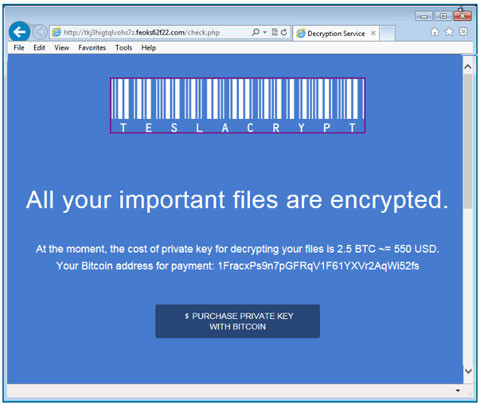
According to Talos, the security research arm of networking communications provider Cisco, hackers have fixed a security vulnerability in the previous versions of TeslaCrypt that enabled users to discover the encryption key and thus decrypt the files that had been locked by the ransomware.
Talos and other security firms such as Kaspersky have previously reverse-engineered versions of TeslaCrypt for corporate clients so that they can retrieve their files without having to pay, and the whole security community has contributed to developing much better detection tools for the ransomware, as well as finding ways to prevent it from being distributed, but for now, there is no way to stop the latest version TeslaCrypt 3 once it is installed on your machine.
"We have shown why TeslaCrypt 3 is one of the most advanced ransomware systems in the world at the moment. It brings strong cryptography and is easy to use for the bad guys. We cannot say it loud and often enough, ransomware has become the black plague of the internet, spread by highly sophisticated Exploit Kits and countless spam campaigns," the researchers write in a blog post explaining the cryptographic algorithm used in TeslaCrypt 3.
"The adversaries are modifying and improving it in every version. Anyone can become a victim if you are hit by a new version, as yet undetected by your AV software. Don't rely on decryption tools, make sure you have backups and that they are up to date."
© Copyright IBTimes 2025. All rights reserved.






















