Ashley Madison hack: Who are Impact Team, why did they leak website data and will they be caught?
In the wake of the sensational publication of the Ashley Madison customer information by hackers known simply as Impact Team, almost all of the media attention has been focused on uncovering the salacious details contained within the data dump. This includes identifying public figures, detailing how people can see if their partners are using the service and generally drooling over the drip feed of gossip and innuendo from the 9.7GB of data.
There has however been very little focus on the people behind the attack – the hacker or hackers who call themselves Impact Team and who carried out one of the largest security breaches of consumer information in history. The main reason for this lack of attention is the fact that very little is known about the hackers, and despite Avid Life Media (ALM) brining in "independent forensic experts and other security professionals" and working with law enforcement agencies including the FBI, the Mounties and the Toronto Police Services, they have been unable to prevent the hackers following through with the threat to publish all the stolen customer data.
Here we will look at what we know about the hackers, what their motivations might be, who they could be and how ultimately they might be caught.
The Facts
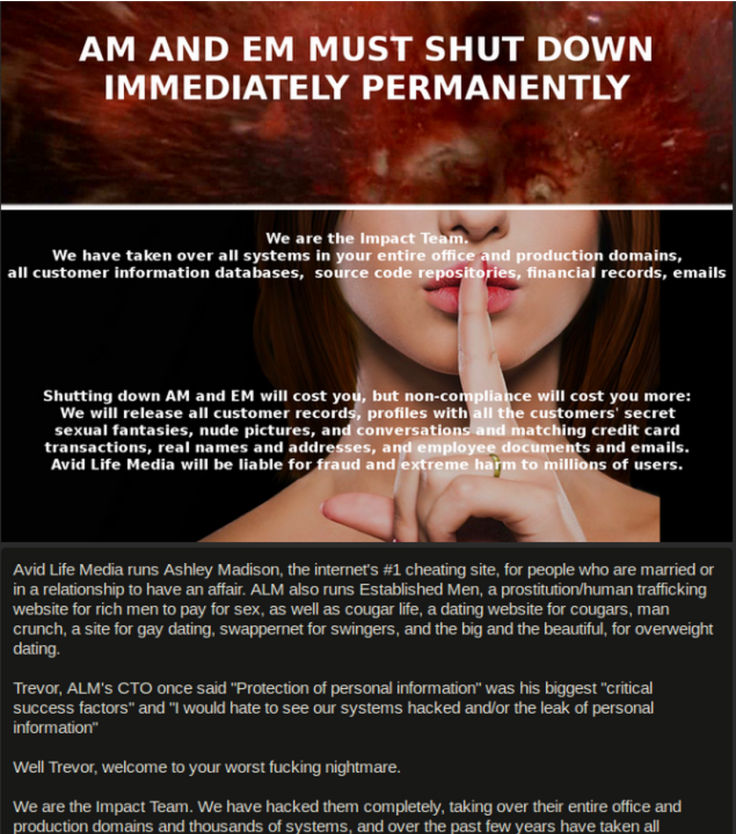
On 19 July, ALM, the parent company of Ashley Madison, Cougar Life and Established Men, confirmed its customer database had been breached with a sample of the database posted online. The hackers also posted a manifesto that warned if ALM did not take Ashley Madison and Established Men offline, they would publish all the customer data.
One month later and the hackers kept their word, posting a link on the dark web to a torrent of the stolen information, which contains some 36 million accounts including names, height, weight, gender, addresses, email address, GPS co-ordinates, credit card transaction details, limited credit card numbers and sexual preferences. While there were older databases with unencrypted passwords included in the dump, the current up-to-date databases contained encrypted passwords.
Why did the hackers do it?
This is a key question in identifying the person or people behind the attack. According to the manifesto (above), which was published in July, the reason the company was targeted was because the company's Full Delete service, which promises to erase all customer data from Ashley Madison's database for a fee of $19 (£12), was a lie: "Full Delete netted ALM $1.7m in revenue in 2014. It's also a complete lie. Users almost always pay with credit card; their purchase details are not removed as promised, and include real name and address, which is of course the most important information the users want removed."
However, the release attached to the data dump this week has more of a focus on the customers, who they accuse of "fraud, deceit and stupidity" telling affected users to "learn your lesson and make amends".
While the vast majority of cybercrime is economically motivated, there doesn't appear to be a financial aspect to this attack. If the attack was carried out for monetary gain, we may never have heard about it, and the hugely valuable personal information stolen would have been traded on the dark web. The hackers could have privately contacted ALM to demand a ransom, but neither the hackers nor the company has mentioned this.
While motivation is a key factor in identifying the culprit of this crime, the fact is that they could simply have been doing it just because they can and it is fun to see so many people scramble to come up with excuses. The motivation of fame and glory that comes with such a high-profile attack also appears to be something that can be ruled out, as we will see below.
Why haven't the hackers been caught?
With ALM working around the clock in conjunction with multiple law enforcement agencies including the FBI, one of the most surprising aspects of this attack is the fact the hackers have not been caught in the month since they publicised the breach.
There are several reasons for this, but the main one is that the hacker's operational security (OpSec) has been excellent (so far). As researcher Erik Cabetas at Include Security has pointed out, the hackers have "no desire to bridge their dark web identities with their real-life identities and have taken many measures to ensure this does not occur".
This means posting links on the dark web which is accessible through anonymity browsers like Tor and utilising an Onion web server, which serves only HTML/TXT content. The hackers also used the MailTor dark web email service to hide their identity. If the hackers have set these up properly, they could never be found says Cabetas.

Security expert Stephen Coty, from Alert Logic, suggests another reason the hackers have not been caught: "Honestly, the FBI has more important hacks to deal with such as Permera and the Office of Personnel Management. Although I am sure they are dedicating resources to this breach I would think they have bigger fish to fry than a release of people having affairs online, especially since most of the females only make up 5% to 10% of the actual users."
ALM, for its part, believes someone, somewhere knows something about the hackers: "We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law, we also know there are individuals out there who can help to make this happen faster."
So who are the hackers?
Security expert Philip Lieberman from Lieberman Software has this to say about cyberattack attribution:
There is a general population of hackers and researchers that troll and test sites on the Internet on a constant basis. This population of attackers is worldwide and motivated by the usual motivations of money, fame, and power. As is the norm in the hacker community, the higher the profile of the attacked site, the greater the prestige to the hacker who discovers a vulnerability and touts it. The general proof of a hack is the publication of the site data or an obvious defacement of the site for other hackers to see.
The short answer in this case however is that no one knows – but even with the limited amount of evidence available, we can make some educated guesses.
If we rule our nation state actors and cybercriminals on the basis of motivation, then we are left with hacktivists and insiders.
Hacktivist groups, such as Anonymous, typically attack companies and governments they see as doing wrong by the citizens of the world. Therefore the attack on Ashley Madison for lying about its Full Delete service seems a good fit. However what does not fit is the publication of millions of people's private information in a bid to get back at a corporation. Add to this the fact that no hacktivist group has claimed credit for the attack (which they traditionally do) and this suggestion seems unlikely.
That leaves us the suggestion that the hacker (or at least one of the hackers) was with a person with knowledge of ALM and the Ashley Madison website. Reports suggest this is the assumption ALM and the FBI are working on, and there are several pieces of information that suggest this could be the case.
The first is down to motivation. A person on the inside would have known intimately how the website operated and would know if the Full Delete service was not doing what it promised. It would also mean that the person would have easier access to the customer data than someone looking to break in from the outside. In relation to this, Cabetas found within the dump files information which implies an attacker was on the database server in question.
Secondly, if you look at the original manifesto, it contains a reference to Trevor, the first name ALM's CTO, and something he once said about protection of personal information. The hackers added the line: "Well Trevor, welcome to your worst f**king nightmare." This personal attack on a single member of the ALM team suggests some deeper resentment (at least to this writer) and backs up the theory that the hackers knew ALM intimately and have an axe to grind with the company.
Will the hackers be caught?
This all depends on whether the hackers want their identity known or if they have made a mistake. If they want the fame and glory, which so far they have eschewed, then the chances of them being caught increases dramatically. Even telling one other person what has happened could scupper their chances of avoiding prosecution as keeping secrets like this is notoriously difficult.
The most likely way the hackers will be caught is though forensic examination of the attack and the data dump. This was how former Anonymous hacker Sabu (aka Hector Monsegur) was identified and Silk Road kingpin Ross Ulbricht was tracked down. A simple server misconfiguration or a single log-on without using the correct VPN settings is all it would take.
© Copyright IBTimes 2025. All rights reserved.






















