French criminals implanting stolen credit card chips into new forged cards [Video]

Criminals are still able to take money from stolen chip and PIN credit cards, even without having the victim's PIN number, as they are creating forgeries with implanted chips that fool the chip and PIN verification process, French cyber-security researchers have revealed. In 2011, computer science researchers at École Normale Supérieure University and the French government-funded research institute CEA were asked to conduct a forensic investigation into a particularly complex case of credit card fraud, and they have finally published a paper about the case.
Soldering stolen chip to another chip
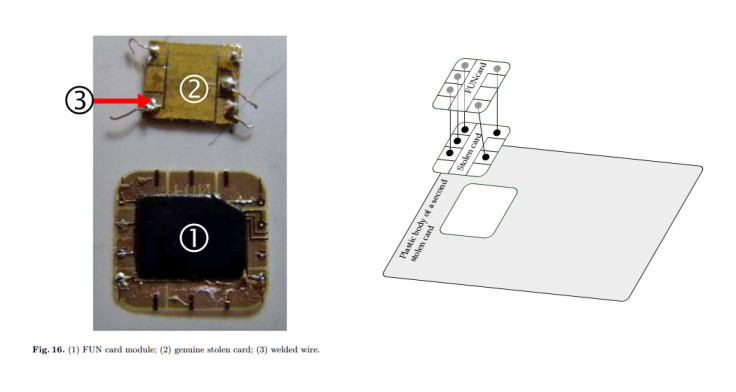
It all started in May 2011 when French banking industry group GIE Cartes Bancaires spotted that credit cards that had been stolen a few months before in France were now being used in Belgium, and they alerted the police. It was discovered that a gang was using specialised software to create card forgeries, and the researchers were eventually asked by the court to determine exactly how the stolen credit cards were being hijacked.
The researchers discovered that the criminals were removing the chip from a stolen chip and PIN credit card and soldering it onto a tiny Funcard chip – a type of open smart card that can read and write memory, which is used by hobbyists and people prototyping new solutions. Then both chips were glued onto the plastic body of yet another stolen credit card, and the Funcard would communicate with the stolen card chip and make it possible for the criminal to bypass chip and PIN security to make purchases.
Even though the new credit card forgery was slightly thicker than a regular card and a bit harder to fit into a credit card reader at a point of sale (PoS) terminal in a shop, the card was still able to pass for a real one without detection. By the time four members of the gang were arrested in France, 40 forged credit cards had been created and the criminals were able to steal just below €600,000 (£441,120, $682,830) in 7,000 transactions.
Attack finally defeated − after six years
"The forensic report produced by the authors of this paper was sufficient for the court to condemn the perpetrators. During our testimony we underlined to the court that this case shows that organised crime is following very attentively advances in information security," the researchers wrote in the report.
"It is important to underline that, as we write these lines, the attack described in this paper is not applicable anymore, thanks to the activation of a new authentication mode Combined Data Authentication (CDA) and network-level protections acting as a second line of defence. Until the deployment of CDA, this fraud was stopped using network-level counter-measures and PoS software updates."
However, although this hacking technique has now finally been defeated by the introduction of CDA, it seems to have taken the banking industry almost six years to acknowledge the flaw and fix it. The Chip and PIN hack was originally first devised by a group of Cambridge University researchers, who used a field-programmable gate array (FPGA) chip, a laptop, a card reader and a handmade card emulator hooked up to a stolen credit card that was hidden in a backpack.
A cable attached to the set-up was connected to a dummy credit card and hidden in the hacker's sleeve, and the hacker then used the dummy card to pay for purchases, while the equipment bypassed the chip and PIN identification security measures.
The Cambridge researchers published their research in January 2010 after alerting the banking industry in December 2009, and the research was explained to the UK public in a feature on BBC Newsnight on 11 February 2010.
Banking industry said it wasn't a real threat
According to Steven Murdoch, a research fellow in information security research at University College London (UCL) who was one of the Cambridge University researchers who took part in the project in 2009, the banking industry dismissed the possibility that criminals could seek to use the exploit in an attack.
"We believe that this complicated method will never present a real threat to our customers' cards. Neither the banking industry nor the police have any evidence of criminals having the capability to deploy such sophisticated attacks," the UK Cards Association said in response to the BBC report.
Now Murdoch is wondering whether the criminals did actually make use of the research, but more importantly, he hopes the banking industry wakes up: "What we do know with confidence is that had the banks acted to close the vulnerability immediately after we notified them, these criminals would not have been able to commit this fraud.
"I hope the banking industry will learn from this lesson when dealing with future vulnerabilities that are disclosed to them — criminals will be as sophisticated as they need to be."
© Copyright IBTimes 2025. All rights reserved.