Hacking Team Tools Allow Governments To Take Full Control of Your Smartphone

Newly published research about Hacking Team's spying tools show the full extent of the control governments can wield against targets' smartphones.
The research shows that governments using the "lawful intercept" tool, known as Remote Control Systems (RCS), can infect iPhones even if they have not been jailbroken, and can take control of a smartphone's camera as well as the microphone to record everything a target is saying.
Documents published by research laboratory Citizen Lab relate to the RCS tool sold by Italian company Hacking Team to governments and law enforcement agencies around the world.
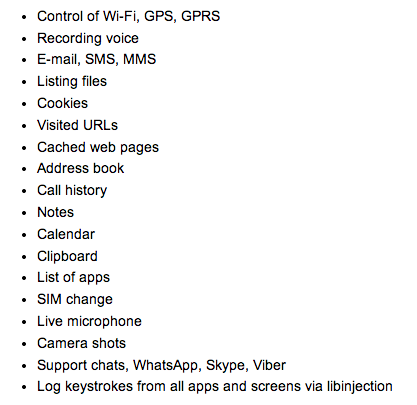
The new documents show that governments can implant a piece of malware on your smartphone and take control of the device's microphone, camera, keyboard and even services like Facebook, WhatsApp and Skype.
The Hacking Team's modules target Android, iOS, Windows Phone and BlackBerry and complement the tools which infect desktop software.
Exceptionally invasive
The documents, which were submitted anonymously, have not been verified but speaking at an event in London on Tuesday, Citizen Labs researcher Morgan Marquis-Boire said that in his opinion the documents were real and reflected the features which were available to governments around the world using Hacking Team's tools.
Hacking Team is one of a number of controversial companies selling sophisticated tools to law enforcement agencies around the world which include the UK-based Gamma International. There has been a lot of negative criticism of these tools as it has been shown on numerous occasions that they have been used to target journalists and human rights activists in the Middle East.
In a blog post on his findings Marquis-Boire said: "This type of exceptionally invasive toolkit, once a costly boutique capability deployed by intelligence communities and militaries, is now available to all but a handful of governments. An unstated assumption is that customers that can pay for these tools will use them correctly, and primarily for strictly overseen, legal purposes. As our research has shown, however, by dramatically lowering the entry cost on invasive and hard-to-trace monitoring, the equipment lowers the cost of targeting political threats for those with access to Hacking Team and Gamma Group toolkits."
Auto-jailbreaking iPhones
In separate research also published on Tuesday, Kaspersky Labs revealed that it has been monitoring the command and control server infrastructure of the RCS and found that the most servers were located in the US (64), followed by Kazakhstan (49), Ecuador (35) and UK (32).
Kaspersky has also uncovered that Apple's iPhone and iPad devices can also be infected even if they are not jailbroken.
Apple has been praised for keeping malware out of the App Store, with only jailbroken devices being affected by malware.
However Hacking Teams manages to circumvent this by using infected desktop machines to first install a jailbreak on the smartphone or tablet when it is connected to the desktop before installing the surveillance tools - with the user none the wiser.
Saudi Arabia targets
The Android malware module is distributed in a different way, with the documents sent to Citizen Labs highlighting one example of how it was used to target people in Saudi Arabia.
Using a fully functional version of the Qatif Today news application bundled with a Hacking Team payload, those downloading the app would see their devices infected.
The genuine 'Qatif Today' app is an Android and iPhone application that provides news and information in Arabic with a special relevance to the Qatif Governorate of Saudi Arabia. The malicious version was not appear on the official Google Play Store but is spread through a Dropbox link.
Analysing this link, Marquis-Boire was able to see that the only people clinking on the link - which was spread on social media - were based in Saudi Arabia.
Anonymous
Among the revelations within the documents provided to Citizen Lab was the use by Hacking Team of a system to anonymise the data being sent back to the command and control servers.
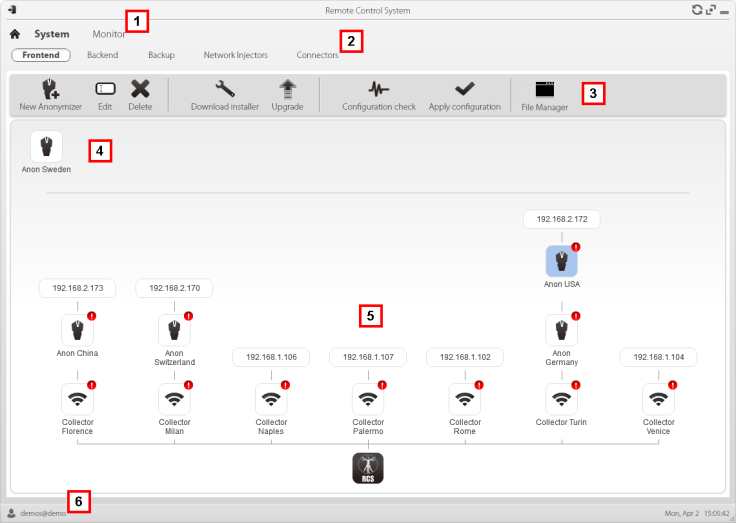
The system, which within the control panel is shown using the same icon used by Anonymous (above), tries to replicate what the Tor network does by bouncing the traffic off numerous nodes around the world before sending it to its final destination.
Another of the leaked images shows that the Hacking Team's mobile modules are able to track the location of infected devices on Google Maps. Citizen Labs highlights that in what is presentation material for new clients to show them the capabilities of the software, it has potentially revealed one of its current customers.
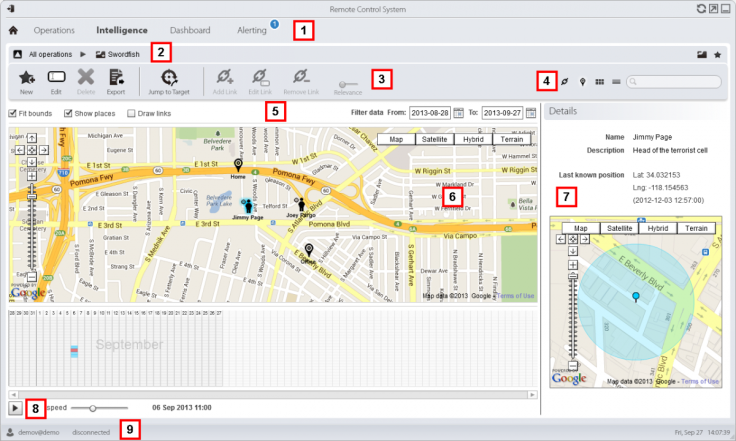
The image (above) shows a device monitoring someone called Jimmy Page being tracked but the location of the target is in the access controlled parking lot of the LA County Sheriff.
© Copyright IBTimes 2025. All rights reserved.






















