Randomness: The fix for today's broken security
Dr. Carsten Stöcker is founder of Spherity GmbH, and Prof. Gideon Samid, PhD, serves as the Chief Technology Officer for BitMint.
A 100 year-old idea, brought to life by modern technology, can protect us from even the smartest hackers, most powerful intelligence agencies and the fastest quantum computers.
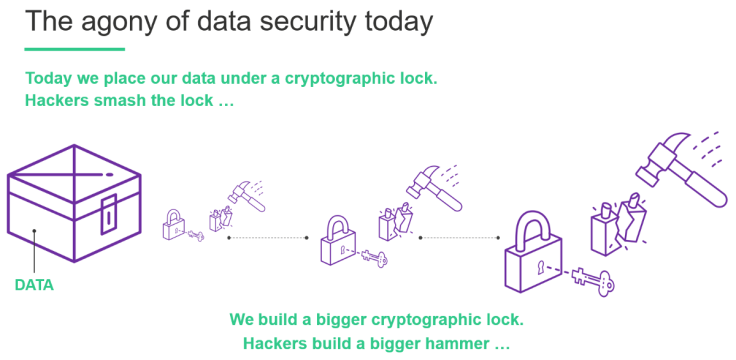
The cyberworld in which we spend our days — and on which our lives depend — is not safe, and is becoming more dangerous all the time. From nation-states trying to sway elections with fake news to ransomware that shuts down hospitals, we are living in a "Wild West" in which any data, or any transaction, may be attacked at any time. And like travelers in a lawless frontier, we are left to scan the horizon constantly for trouble, scrambling to plug the leaks in defenses we don't quite trust.
We are vulnerable not just because of the increasing sophistication of hackers, who are today as likely to be well-funded criminal organizations or governments as petty thieves or amateurs out for the thrill of defacing a website. Nor is the greatest threat the development of new offensive tools such as quantum computers, which might soon be powerful enough to crack today's most widely used cryptographic ciphers. The biggest problem is that our basic approach to cyber security is flawed.
In a Battle of Wits, You Will Always Lose
By its very nature, in a battle of wits, you win some, and you lose some. But our security loses are too painful, and too costly.
Think of how we, or our organizations, handle security today. We try to build systems that are inherently safe, and spend fortunes on everything from firewalls to antivirus software and teams of penetration testers. But most of these are tactical responses to individual types of threats, not a proactive and comprehensive approach to safeguarding all of our data and transactions, all the time, against any threat.
Hackers find a new vulnerability in Windows and Microsoft issues a patch, which we may or may not get around to installing. A new ransomware attack surfaces and antivirus vendors add it to their list of threats to scan for. The attackers make a slight change in their code and the antivirus vendors add that variant to their list. New technologies such as the Internet of Things expand the attack surface and we scramble for new point solutions (and new penetration tests) to protect them, but usually only after a successful breach shows us where the vulnerabilities lie.
But the most dangerous flaw lies in our approaching security as a battle of human wits and computing horsepower. Ingenious hackers wrack their brains to exploit weaknesses in applications, operating systems, networks and encryption protocols. We wrack our brains to fool them, or to predict their next attack. Alas, even if one attacker out of many outwits us, we lose.
Today's "world class" security is based not on randomness, but on our (over)confidence in the math underlying our cryptography. This is inherently vulnerable to a mind like that of Alan Turing, whose singular brilliance proved decisive in breaking the German Enigma code in World War II. Unfortunately we don't know how many "Alan Turings" work against us in this raging cyber war. Yet, the conventional wisdom binds us to a "math v. math" battleground in which we cannot win often enough to be safe.
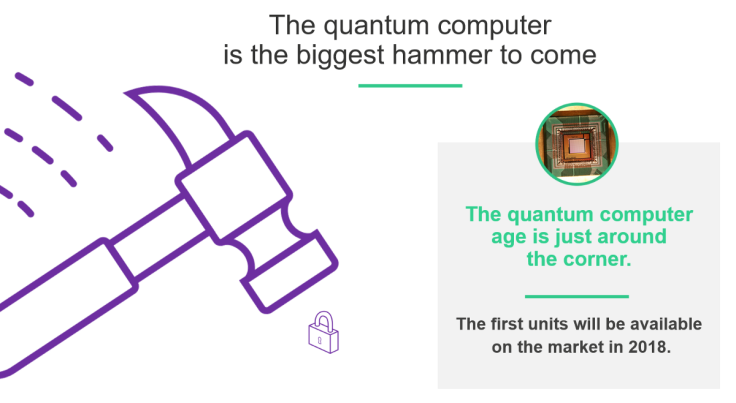
And with each passing year, the odds favor the attackers more as the worldwide reach of the Internet and cloud computing serve as raw meat to better equipped hackers, and shadowy gangs of "Alan Turings". If all that weren't bad enough, the amount of computing power available to the attacker is about to expand exponentially with the advent of quantum computers. These will soon be able to efficiently solve the cryptographic math problems that protect most of today's digital signatures, hash and encryption functions. When such quantum computers become available (in years or even months) our IT systems will be even more vulnerable than they are now.
Forget Being Smart. Be Random.
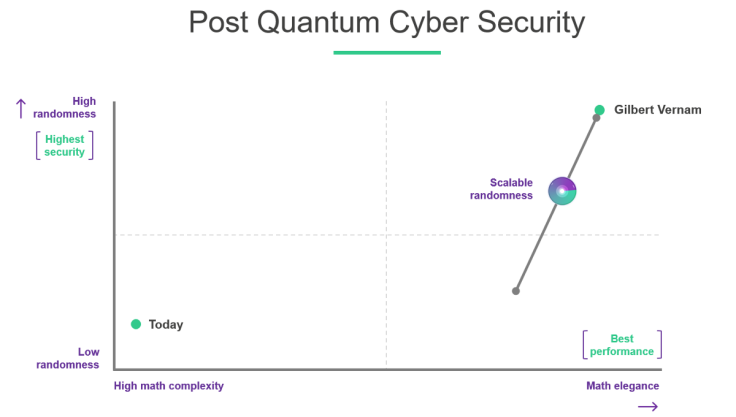
The use of random combinations of letters and numbers to "scramble" data so it cannot be read is as old the first codes and is at the heart of all modern cryptography. Even the best cryptography can, however, be broken because the randomness is used sparingly, and the hackers know how much was used and, thus, how much guessing they must do to break the code.
Ironically, the answer to our most modern security woes was invented 100 years ago, by a mathematician named Gilbert S. Vernam. He patented a cipher which used no mathematical complexity but instead called for large amounts of randomness. He took a page from the then-new theories of quantum mechanics, which told us that at the subatomic level, at the very heart of the universe, events are truly random. What if, he proposed, we could tap enough of that true randomness to make it impossible for even the smartest person with the best equipment to uncover the true message?
Even today, the Vernam Cipher is the only security mechanism that has been mathematically proven to be unbreakable. If it is so effective, why hasn't it been used? Two reasons, each of which is rapidly disappearing:
- The high cost of storing and processing large amounts of random information. In the days of paper ciphers and human (rather than electronic) processing, there was no remotely feasible way of handling the amounts of randomness required to make the Vernam cipher work. Today, the rapid and continuous decline in the cost of processing power, and of storage, make it feasible to process the amount of "randomness" required by the Vernam cipher on even common mobile devices such as smart phones.
- The lack of truly random information. While many of today's encryption algorithms make use of "random" sequences of letter and numbers, under the hood, that "randomness" is generated by a non-random computer program. However clever or complex the program, it is still based on an underlying pattern that a smart enough person (or powerful enough computer) could reverse engineer to discover the pattern, and thus, the underlying information. Today, relatively small and inexpensive random number generators tap quantum fluctuations at the atomic or photonic level to produce true randomness in the quantities required by the Vernam cipher.
The use of massive amounts of true randomness — what we call Post Quantum Cyber Security — turns today's model, based on complex mathematical ciphers, on its head. This true randomness protects us from hackers who are smarter than we expect. Relying on randomness, rather than mathematical complexity, allows the owner of the data to choose how much randomness to use and thus how much security to defend her data with.
Post Quantum Cyber Security with User-defined RandomnessA related technology, Quantum Key Distribution (QKD) will play an important role. QKD uses the fundamental principles of quantum mechanics to create and share large random encryption keys and to establish secure communication channels among users.
Next Steps: Post Quantum Cyber Security
IT Systems and IoT devices that are deployed today stay in the field for many, many years, some IoT devices have a life cycle of 30+ years. To protect our civil order we are calling for responsible leadership to start preparing our systems for the post quantum area now.
We recommend a three-step approach to implementing the Post Quantum Cyber Security needed to protect our systems from today's, and tomorrows, threats.
1. Research, test and deploy Post Quantum cryptographic primitives including ciphers with built in randomness.
2. Learn how to build security around large amount of true, non-algorithmic randomness, systematically eliminating "pseudo" randomness based on algorithms (e.g. use Quantum Random Number Generators) and
3. Research, test and deploy quantum key distribution.

Quantum Random Number Generator Hardware (Source: ID Quantique SA). QRNDs are in the process of shrinking to much smaller, low-power components for the use in IoT devices.The ability to finally achieve true, cost-effective security, once and for all, is finally within our grasp, with Post Quantum Cyber Security solutions available from companies such as BitMint, Cambridge Quantum, China Quantum Technologies, Crypta Labs, Dyadic, ID Quantique and Post Quantum.
In fact, randomness can even protect new technologies such as blockchain (distributed ledgers that allow trusted transactions, or even the use of alternative currencies such as Bitcoin) from attacks by quantum computers — using quantum protection to defend against quantum threats. For instance GazpromBank recently announced it successfully tested a QKD-enabled new blockchain technology among three of their corporate facilities.
China will soon deploy the world's largest "quantum optical fiber communications system" connecting Shanghai and Beijing over a distance of 2000 km. As a further evolution China is evaluating to implement a quantum communications network among the some of the biggest Asian and European cities by 2020 with plans to extend the network globally by 2030.
Today, entire economies and public infrastructure rely on the security of smart devices linked by the global Internet. Tomorrow, our everyday lives will rely on the security of such devices, ranging from medical implants to self-driving cars. The stakes are becoming too high to wait for hackers to find vulnerabilities for us, and to keep hoping "our" experts are smarter than theirs, and "our" computers more powerful than theirs.
For the good of the global economy, our democratic institutions and our personal well-being, we urgently need to take a new road to information security. Einstein and his fellow physicists were shocked to discover that randomness rules the physical universe. We are equally surprised to realize that randomness can rule cyber space as well. Physicists have quickly turned around to exploit their discovery. For the sake of our data, our systems and our societies, we should do the same.
About the authors:
Dr. Carsten Stöcker is founder of Spherity GmbH. Spherity is a scalable decentral platform for the fourth industrial revolution providing secure identities and digital twins bridging the physical, biological and digital spheres. He is a physicist by training with a Ph.D. from the University of Aachen. He also serves as a Council Member of Global Future Network for the World Economic Forum. Prior to founding Spherity GmbH, Dr. Stöcker worked for innogy SE, German Aerospace Center (Deutsches Zentrum für Luft- und Raumfahrt, DLR) and Accenture GmbH.
Prof. Gideon Samid, PhD, serves as the Chief Technology Officer for BitMint, developing a robust global, legacy-friendly framework for digital money and cyber security. A critically acclaimed author and columnist, promoting the role of randomness as the foundation for a safe, secure, and reliable cyber universe.