Recover Cryptolocker Encrypted Files Using Free Decryptolocker Tool

Security researchers have launched Decryptolocker, a free tool which will unlock files you may have lost forever by the pernicious Cryptolocker ransomware.
The Cryptolocker ransomware rose to prominence in 2013 and has elicited millions in ransoms from its victims. It is reported to have infected more than 600,000 systems globally.
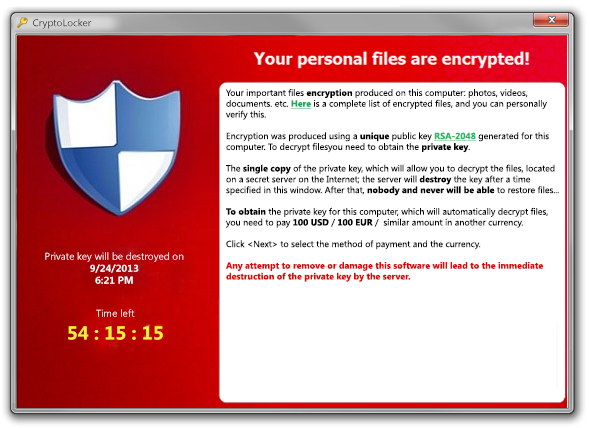
Once your system is infected, Cryptolocker encrypts all your files, and issues you with a ransom demand, warning that if you don't pay up within a specified amount of time, your files will be locked forever.
And until now, that was certainly the case as the encryption used by the creators of Cryptolocker is seen as almost uncrackable.
Decryption
However researchers at FireEye and Fox-IT have come together to create Decryptolocker.
The online service is simple to use:
- Go to the Decryptolocker website and upload a single encrypted file you want unlocked
- Wait for the service to email you a private key and a link to a decryption tool.
- Download the tool and run locally on your machine.
- Use the private key and unlock all encrypted files on your hard drive.
The researchers warn that you shouldn't upload any file which contains sensitive material, but if that is all you have, the service should work just as well - it's just not good practice.
The researchers have not however cracked the intenetrable encryption used by the hackers behind the ransomware, but they were able to create this tool after accessing the criminals' database of private keys, Fox-IT's Ronald Prins confirmed on Twitter
Slavik
While the Cryptolocker encryption remains in place, at least this gives anyone effected by the ransomware an option to unlock their files without having to pay the ransom.
Cryptolocker is operated by a gang of criminals from Russia led by Evgeniy Mikhailovich Bogachev (aka Slavik) who is also responsible for spreading the GameOver Zeus malware.
Earlier this year the FBI placed Bogachev on its most wanted list with a reward on offer for information that leads to his arrest.
Andy Chandler, senior vice president of Fox-IT, told Graham Cluley that his company has been tracking Bogachev for months, and in partnership with FireEye "a clear picture of the criminal group has emerged".
© Copyright IBTimes 2025. All rights reserved.






















