The rise and fall of PwnedList: How 866 million hacked passwords were exposed all over again

PwnedList launched in 2011 with the best intentions. Yet now, five years later, the service that allowed users to check if their emails and passwords had been compromised by a data breach is being "decommissioned" after leaving its entire 866 million-strong database of credentials wide-open to exploitation.
At launch, the service worked by scanning PasteBin and torrent websites for hacked information and at one point claimed to be inputting upwards of 40,000 new accounts every week. After six months, the database was said to contain roughly 10 million entries. However, this progress has come to a halt after the discovery of a security flaw by a researcher called Bob Hodges, who stumbled on serious issues when attempting to add domains he owned to a PwnedList "watchlist".
This, in theory, should have alerted him to any future hacking incidents but instead Hodges found he could monitor any domain he wanted by circumventing the usual approval process users had to go through before adding information to a watchlist by using a method called parameter tampering. Essentially, the flaw meant anyone could request millions of the stored accounts with ease.
Hodges approached infosec writer Brian Krebs, who first reported on the vulnerability on his website KrebsOnSecurity. The flaw was double-checked by Krebs, who was able to use it to download "more than 100,000" usernames and passwords of stored accounts ending in apple.com with one simple request.
"I was able to replicate Hodges' findings, successfully adding apple.com to my watchlist," Krebs explained in a blog post. "I also found I could add basically any resource I wanted. Although I verified that I could add top-level domains like .com and .net, I did not run these queries because I suspected that doing so would crash the database, and in any case might call unwanted attention to my account."
He continued: "The report I was then able to download included more than 100,000 usernames and passwords for accounts ending in apple.com. The data was available in plain text, and downloadable as a spreadsheet [...] this simple security flaw may have inadvertently exacerbated countless breaches by preserving the data lost in them and then providing free access to one of the internet's largest collections of compromised credentials."
In response to the findings, InfoArmour, the parent company of PwnedList that created a business model around the email-checking technology, downplayed the risk of the findings. "The data that was 'exposed' has already been 'compromised' – there was no loss of PII [personally identifiable information] or subscriber data," it wrote on Twitter.
On Krebs, the data that was “exposed†has already been “compromised†- there was no loss of PII or subscriber data.
— InfoArmor (@InfoArmor) May 2, 2016
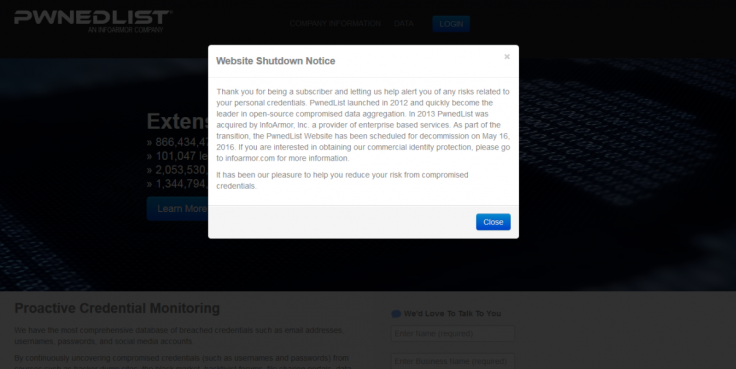
However, the incident has since proven fatal for the service. A pop-up window on the website now states: "The PwnedList website has been scheduled for decommission on May 16, 2016. If you are interested in obtaining our commercial identity protection, please go to infoarmor.com for more information. It has been our pleasure to help you reduce your risk from compromised credentials."
Troy Hunt, the researcher behind HaveIBeenPwned, which also lets users check if they have been impacted by a cyberattack or security breach, commented that storing passwords is always "a huge risk." Referencing the fall of PwnedList, he said: "This is precisely why I decided from day one that HaveIBeenPwned will never store passwords."
Cyberattacks and breaches continue to plague internet users, governments and businesses across the globe. Most recently, hackers have targeted election systems in Mexico and the Philippines. Meanwhile, a massive breach at the Qatar National Bank (QNB) resulted in the leak of names, addresses and credit card information on thousands of customers.
© Copyright IBTimes 2025. All rights reserved.






















