TeslaCrypt ransomware shut down by developers 'sorry' for ruthless extortion campaign

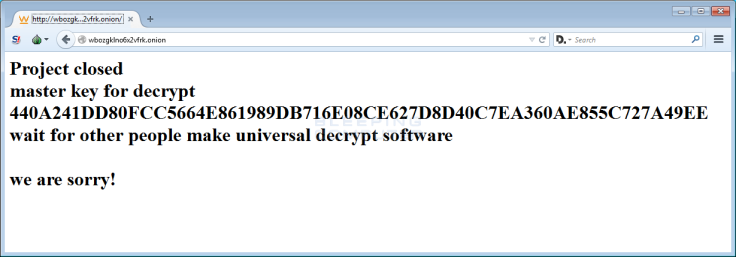
The developers of the notorious TeslaCrypt ransomware have claimed to be shutting down their operation – not only releasing a master decryption key but even apologising for causing years of mayhem.
The revelation comes from a security researcher working for Slovakia-based security firm ESET, who made contact with the TeslaCrypt developers through a 'support channel' on the dark web usually reserved for victims of the Trojan malware to make payments in order to regain access to their locked computer files.
Surprisingly, the cybercriminals admitted they were closing down the 'project' and even offered the researcher a free-to-use master decryption key. Furthermore, a note said: "We are sorry!" If it turns out to be a legitimate apology, it's an extremely rare change-of-heart in the world of cybersecurity.
According to Lawrence Abrams, from Bleeping Computer, security experts noticed a decline in use of TeslaCrypt in recent weeks – with ransomware distributors instead moving to a strain called CryptXXX.
First detected back in February 2015, TeslaCrypt quickly gained notoriety for targeting computer PC gaming-related files and extensions while distributing the Angler exploit kit to unwitting victims. Additionally, by spreading via email phishing campaigns and malicious adware, it could also infect Word, PDF and JPEG files before holding their contents to ransom.
Yet with the master decryption key in the wild it didn't take long for crypto-experts to develop a cure. The key provided by the TeslaCrypt operators works for both TeslaCrypt v3 and v4 infections and extensions including .xxx, .ttt, .micro, and .mp3, ESET said in a blog post. Additionally, both ESET and a long-time ransomware fighter called BloodyDolly have announced fresh fixes that will allow infected users to unlock encrypted files, documents and pictures.
It remains unclear if the former TeslaCrypt engineers have abandoned the extortion business altogether or simply moved on to another strain of malicious software. The latter is extremely likely, especially given that TeslaCrypt was starting to crumble under the weight of a multitude of decryptors that were making it less effective when used.
That's not to say it was not feared online. When compared to other notorious strains, including Locky and the well-known CryptoWall, a recent study by security firm Fortinet found TeslaCrypt was still the third most popular piece of ransomware used in the first three months of the 2016.
In any case, ESET researchers continue to caution internet users on the dangers posed by ransomware – which recently hit the headlines after being used against a major hospital in the US and locking down crucial computer systems.
The firm said: "We must stress that ransomware remains one of the most dangerous computer threats at this moment, and prevention is essential to keep users safe [...] we advise all users to be very careful when clicking on links or files in their email or browsers. This is particularly true when messages are received from unknown sources or otherwise look suspicious."
© Copyright IBTimes 2025. All rights reserved.






















