iOS 8.1.3 jailbreak status update: Apple kills several exploits in new update

Apple has reportedly patched several jailbreak exploits unearthed in Pangu, TaiG and PP jailbreak with the release of iOS 8.1.3 for iPhone, iPad and iPod Touch.
Prospective jailbreakers are advised to avoid updating their iOS device to the latest firmware in order to preserve existing jailbreak tweaks and apps.
Apple has revealed the various exploits that are patched up in iOS 8.1.3 via its support article, wherein it clearly credits Pangu, TaiG as well as i0n1c (aka Stefan Esser) for their work in utilising these exploits for making jailbreak tools.
Some of those noteworthy jailbreak exploits that are patched up by Apple's newest iOS firmware update are listed below:
dyld
Available for: iPhone 4s and later, iPod Touch (5th generation) and later, iPad 2 and later
Impact: A local user may be able to execute unsigned code
Description: A state management issue existed in the handling of Mach-O executable files with overlapping segments. This issue was addressed through improved validation of segment sizes.
CVE-ID
CVE-2014-4455 : TaiG Jailbreak Team
AppleFileConduit
Available for: iPhone 4s and later, iPod Touch (5th generation) and later, iPad 2 and later
Impact: A maliciously crafted afc command may allow access to protected parts of the filesystem
Description: A vulnerability existed in the symbolic linking mechanism of afc. This issue was addressed by adding additional path checks.
CVE-ID
CVE-2014-4480 : TaiG Jailbreak Team
IOHIDFamily
Available for: iPhone 4s and later, iPod Touch (5th generation) and later, iPad 2 and later
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A buffer overflow existed in IOHIDFamily. This issue was addressed through improved size validation.
CVE-ID
CVE-2014-4487 : TaiG Jailbreak Team
Kernel
Available for: iPhone 4s and later, iPod Touch (5th generation) and later, iPad 2 and later
Impact: Maliciously crafted or compromised iOS applications may be able to determine addresses in the kernel
Description: An information disclosure issue existed in the handling of APIs related to kernel extensions. Responses containing an OSBundleMachOHeaders key may have included kernel addresses, which may aid in bypassing address space layout randomisation protection. This issue was addressed by unsliding the addresses before returning them.
CVE-ID
CVE-2014-4491 : @PanguTeam, Stefan Esser
Kernel
Available for: iPhone 4s and later, iPod Touch (5th generation) and later, iPad 2 and later
Impact: Maliciously crafted or compromised iOS applications may be able to determine addresses in the kernel
Description: The mach_port_kobject kernel interface leaked kernel addresses and heap permutation value, which may aid in bypassing address space layout randomization protection. This was addressed by disabling the mach_port_kobject interface in production configurations.
CVE-ID
CVE-2014-4496 : TaiG Jailbreak Team
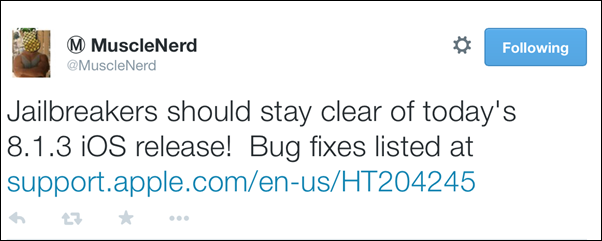
As Redmond Pie reports, MuscleNerd has also confirmed that the jailbreakers should stay away from updating their device to latest iOS 8.1.3 release.
Here is what MuscleNerd had to tweet in his message to avid jailbreakers and his followers, regarding the iOS 8.1.3 jailbreak status update:
On the contrary, those who are eager to update their iOS 7 or iOS 8 devices to iOS 8.1.2 can do so, as Apple is still signing the previous firmware.
Updating to iOS 8.1.2 will also enable jailbreakers to jailbreak their device with TaiG or PP jailbreak, and thereby install the latest jailbreak tweaks and apps.
However, there is still no word on the status or the release of iOS 8.1.3 jailbreak from any of the leading developers including evasi0n, Pangu, TaiG and PP jailbreak teams.
© Copyright IBTimes 2025. All rights reserved.






















