ShoCard raises the bar for digital identity using blockchain
A large US bank recently said it counts its success on how many branches it can close down. This reversal being brought about by digitalisation is a trend that comes with a greater risk of fraud and identity theft, which means financial institutions are increasingly looking for ways to raise the bar for authentication of users.
Palo Alto-based ShoCard uses blockchain technology to raise that bar, while also making a mobile device handle all the necessary processes of certification and verification. Armin Ebrahimi, the founder and CEO of ShoCard, told IBTimes his company is close to making announcements involving a couple of banks and a well-established KYC checking company.
He said: "We are currently in Beta with the KYC company and we will be announcing it in the early part of the first quarter of 2016. The other two banks we are working with have their teams here in the US, but both of them have an international footprint. They are doing internal testing on the product right now, and we expect them to go into beta later in the year; they go through various phases of it and I think what they are going to do right now is still a limited internal beta.
Ebrahimi is a former head of platform engineering at Yahoo where he worked for over 10 years and where he dealt with fraud and identity. Being a very large scale operation, Yahoo faced its fair share of account takeovers, hacking, phishing and robots that pretended to be real users. Latterly, he has combined a focus on mobile, with a fascination for blockchain technology. The end result is ShoCard.
"The idea of ShoCard was to create a digital identity where the users are in control of their private data. It remains with them on their devices and they decide who to share that with; there's not some central place where someone could go and hack into the data and access it," he said.
The blockchain is the means of validation and verification, allowing anyone to look at the data path. The data itself is encrypted so no one can intercept it, or look at it on the blockchain without the user's permission. The system uses the Bitcoin blockchain. "We are not dependent on the Bitcoin blockchain but it's big enough and readily acceptable so it makes a lot more sense for us to be using that," said Ebrahimi.
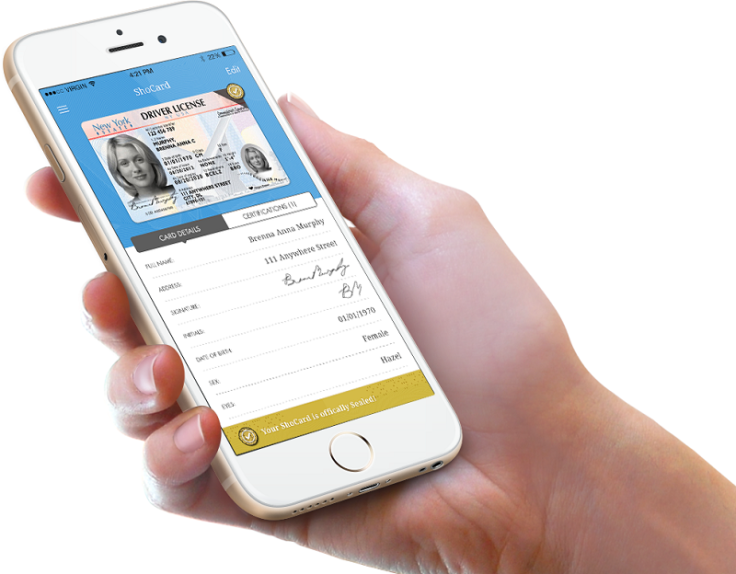
To register a ShoCard involves a certification process. "You scan a drivers licence or passport, and we grab the individual field within that, such as your name, licence number, passport number, date of birth – all of that information individually. We create a hash for that. Then we use the private key that's on the mobile device to create a digital signature of that hash, and that's the piece that we end up putting on the blockchain. We put these various fields together in one record to create an ID for that user.
"If the user then provides the raw data with a public key and a pointer to that record on the blockchain, the data can be verified. So you can create a correlation between the data that the user has on the mobile device and what's on the blockchain," said Ebrahimi.
Following the registration process, users can be certified by some other trusted party such as a bank or KYC checking company, which then issues a certification for the user. "They use their own private key to write the records on the blockchain, pointing to that user's record entry that's also on the blockchain. We call that your ShoCard ID. Those are the two steps: one is the registration where we put hash signatures of the individual fields on the blockchain, the second one is a certification."
The system also provides a secure work-around in cases when your bank suspects a credit card transaction could be fraudulent and wants to reject that transaction. "They can send you a notification – a very secure notification – saying is this really you and do you authorise this transaction? Then we use things like touch ID, each time we access a private key to answer those questions. We never do anything in clear text because we believe that those ultimately can be hacked."
"So the use cases ultimately are: being able to authenticate the user whenever you do any kind of transaction – be it logging into a website, calling a call centre, authenticating a transaction – but being able to do that with the confidence that we know it's you, and being able to do that incredibly quickly," said Ebrahimi.
© Copyright IBTimes 2025. All rights reserved.






















