iOS 7.1.1 Untethered Jailbreak: i0n1c Explains How Exploit Code Works

Stefan Esser (aka i0n1c) explains the working principle behind the exploit code used in his latest untethered jailbreak for iOS 7.1.1 via a recent post on SektionEins.de.
According to the post, the jailbreak uses a kernel bug that is hidden inside some app functionality and can be easily activated within the iOS application sandbox. It means the exploit code can be used to break out of any application that is being exploited.
Further elaborating on the jailbreak exploit's working principle, i0n1c had this to say:
This is very different from nearly all of the kernel vulnerabilities used in iOS jailbreaks since iOS 4. There have been only 2 publicly disclosed vulnerabilities that had this power. The first has been used in comex's JailbreakMe3 and the other one is the posix_spawn() vulnerability disclosed by SektionEins during SyScan 2013 and later used by the jailbreak community in the p0sixpwn jailbreak.
Potential initial injection vectors for the kernel exploit are:
- exploit against an internal app like MobileSafari
- exploit against any vulnerable app from the AppStore
- exploit from within a developer/enterprise app
i0n1c further explains that it is quite easy to implement this exploit as several Safari/webkit Vulnerabilities surface online every month, while AppStore apps link to older and vulnerable libraries that can be easily exploited.
In addition, the backup files from AppStore apps always remain on the system and can be re-exploited for future use. The hacker plans to show this exploit in action in the next few weeks.
i0n1c also reports that the jailbroken iOS 7.1.1 device enabled him to identify the stack-guard stack canary vulnerability which was publicly disclosed in April 2013 ( at SyScan 2013 security conference) is still unfixed in latest iOS as well as Mac OS X versions.
Here is the complete description of the bug and its working concept, as detailed by i0n1c:
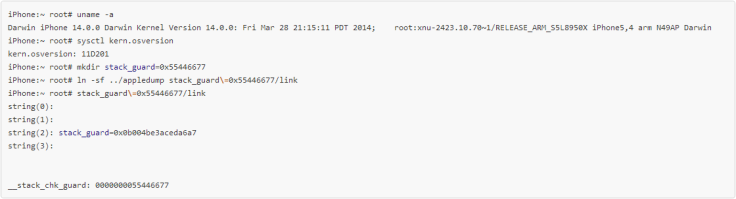
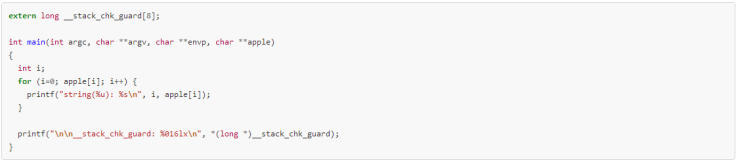
The bug in question allows a local attacker to call a target executable in a way that he controls the value of the stack_guard stack canary that is used to stop stack buffer overflow vulnerabilities from being exploitable. This vulnerability therefore renders the stack canary mitigation in iOS useless against local attackers. For iOS this means that local attacks (persistence/untethering) that rely on stack buffer overflows are suddenly exploitable again or easier to exploit, because the attacker can control the value of the stack_guard.
The bug is caused by libc scanning through the apple strings that are passed by the kernel to an executable for the value of the stack_guard canary value.
For instance, an attacker could activate the execution of the binary through a symbolic link to control this canary, concludes i0n1c.
Here is the complete exploit code (see screenshot below) including the appledump code related to the Stack Canary vulnerability:
© Copyright IBTimes 2025. All rights reserved.






















